Information and Communications Technology: DOD Needs to Fully Implement Foundational Practices to Manage Supply Chain Risks
Fast Facts
IT and communications technologies use parts and services from around the globe. Emerging threats in the supply chain for these technologies can put federal agencies—including DOD—at risk. For example, communications hardware with compromised components could lead to the loss of sensitive data.
Of our practices for managing agency-wide supply chain risks, DOD addressed 4 and partially addressed the other 3. Specifically, DOD still needs to update and finalize an agency-wide strategy and implement processes for reviewing potential suppliers and detecting counterfeits. We recommended committing to a time frame for addressing these issues.

Highlights
What GAO Found
The Department of Defense (DOD) has fully implemented four and partially implemented three of seven selected foundational practices for managing information and communications technology (ICT) supply chain risks (see figure). These risks include threats posed by counterfeiters who may exploit vulnerabilities in the supply chain. Supply chain risk management is the process of identifying, assessing, and mitigating the risks associated with the global and distributed nature of ICT product and service supply chains.
Assessment of the Department of Defense's (DOD) Implementation of Selected Foundational Information and Communications Technology (ICT) Supply Chain Risk Management Practices
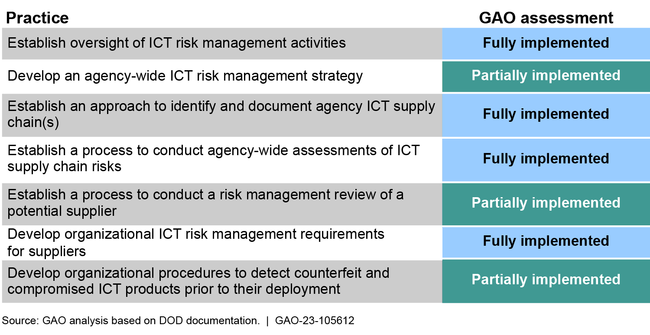
By fully implementing four of the foundational practices, DOD has taken steps to mitigate potential threats and secure its ICT supply chain. Regarding the three partially implemented practices, the department has begun several efforts that are not yet complete. For example, the department has developed a risk management strategy but has not approved guidance for implementing it. DOD has also piloted the use of several tools to review potential suppliers but the review of the results is ongoing. However, DOD did not specify time frames for when these actions would be completed. Fully implementing the three remaining practices would enhance the department's understanding and management of supply chain risks.
DOD provided leadership and support for several government-wide efforts to protect the ICT supply chain. For example, the department offered a course and assisted small businesses in protecting their supply chains. Additionally, the department developed an action plan to facilitate cyber threat sharing and briefed a federal acquisition community of practice on performing cyber test and evaluations. DOD also shared ICT supply chain responsibilities as a member of the Federal Acquisition Security Council. Further, the council has the authority to issue exclusion orders to prevent purchasing from suppliers that may be compromised.
Why GAO Did This Study
Federal agencies rely extensively on ICT products and services (e.g., computing systems, software, and networks) to carry out their operations. However, agencies face numerous ICT risks that can compromise the confidentiality, integrity, or availability of an organization's systems and the information they contain.
Senate Report 117-39 accompanying the Fiscal Year 2022 National Defense Authorization Act included a provision for GAO to provide an assessment of DOD's efforts to address ICT supply chain risks. The specific objectives for GAO's report were to (1) assess the extent to which DOD is implementing foundational ICT supply chain risk management practices and (2) describe the extent to which DOD is leading or supporting government-wide efforts to protect the ICT supply chain.
GAO compared the department's policies, procedures, and related documentation to seven foundational practices. These practices are based on National Institute of Standards and Technology guidance for ICT risk management. In addition, GAO analyzed documentation describing DOD's efforts to lead or support government-wide efforts to protect its supply chains. GAO also interviewed relevant agency officials.
Recommendations
GAO is making three recommendations to DOD to commit to time frames for fully implementing the remaining foundational practices in its ICT supply chain risk management efforts. DOD concurred with the recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Defense | The Secretary of Defense should direct the DOD CIO to commit to a time frame to fully implement an agency-wide ICT SCRM strategy, including how the department will assess, respond to, or monitor ICT supply chain risks across the life cycle of ICT products and services. (Recommendation 1) |
The Department of Defense (DOD) concurred with this recommendation and has implemented it. In July 2024, DOD finalized its information and communications technology (ICT) strategy titled, "Strategy and Implementation Plan for ICT and Services Supply Chain Risk Management Assurance". This strategy describes an agency-wide assessment process that includes identifying and assessing risks using software and hardware analyses as well as behavioral testing. In addition, the strategy describes response and mitigation efforts such as isolation and revalidating specific controls before returning to service. Regarding monitoring ICT SCRM, the strategy indicates that DOD will enhance existing processes such as acquisition and program management and in certain instances develop databases and measurement capabilities. As a result of implementing its ICT strategy, DOD decision makers should have the organizational context needed to better manage ICT supply chain risks.
|
| Department of Defense | The Secretary of Defense should direct the Undersecretary of Defense for Acquisition and Sustainment and the DOD CIO to commit to a time frame to fully implement a process to conduct SCRM reviews of potential suppliers. (Recommendation 2) |
The Department of Defense (DOD) concurred with this recommendation and plans to implement it by December 2025. In July 2024, DoD provided a document that indicated that the department is in the process of updating DOD policy documents as needed to address all departmental information and communications technology acquisitions and associated suppliers. We will continue to monitor the department's actions to implement this recommendation.
|
| Department of Defense | The Secretary of Defense should direct the Undersecretary of Defense for Acquisition and Sustainment and the DOD CIO to commit to a time frame to fully implement organizational counterfeit detection procedures for products prior to deployment. In doing so, the department should take into consideration the results of its pilot efforts of applicable tools. (Recommendation 3) |
The Department of Defense (DOD) concurred with this recommendation and plans to implement it by March 2025. In July 2024, DOD provided a document indicating that it will continue to pilot ICT counterfeit and white label protection efforts and communicating results across the department. In addition, DOD components will conduct their own pilots to meet their specific requirements. We will continue to monitor the department's actions to implement this recommendation.
|
