Identity Verification: GSA Should Demonstrate Its Implementation of Policies for Testing Data Backups on Login.gov
Fast Facts
Data breaches at federal agencies could compromise millions of Americans' sensitive information. To reduce the threat of identity fraud, the General Services Administration launched Login.gov—an online tool that many federal agencies use to verify the identities of their website users.
Login.gov largely implemented federally-recommended data protection practices.
However, it didn't fully implement procedures to test the integrity of its backup data. Such testing can help reduce the impact of data loss in the case of a breach.
Our recommendation is for GSA to ensure that Login.gov tests its data backups.

Highlights
What GAO Found
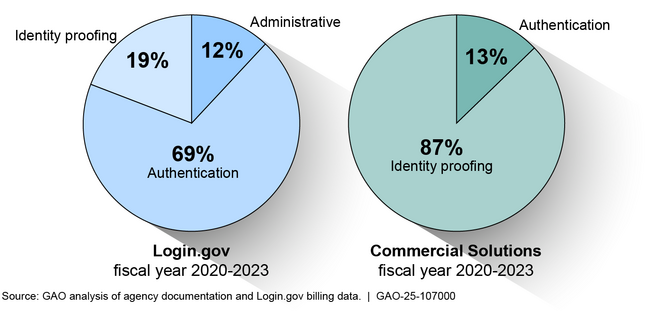
In 2017, the General Services Administration (GSA) launched Login.gov, which offers various capabilities. These include multi-factor authentication, identity-verification services, and fraud prevention measures. Authentication verifies the identity of a user, process, or device before allowing access to IT systems. Identity proofing verifies whether individuals are who they claim to be. However, from fiscal years 2020 to 2023, Login.gov offered fewer capabilities compared to commercial solutions (e.g. biometrics). For example, Login.gov did not provide identity proofing services in alignment with the National Institute of Standards and Technology's standards until October 2024.
Between fiscal years 2020 and 2023, federal agencies reported spending approximately $209 million on commercial solutions while spending $32.5 million on Login.gov.
Agencies' Login.gov and Commercial Solution Spending for Fiscal Years 2020 to 2023
Note: For proprietary reasons, private vendors did not share detailed pricing information on their commercial solutions. As a result, we were not able to make a direct comparison.
Login.gov and selected commercial solutions largely implemented data protection categories in the “protect” function suggested by National Institute of Standards and Technology. Although Login.gov fully implemented four of five privacy practices, it did not fully implement policies and procedures for testing the integrity of its backup data.
According to GSA, the control was not fully implemented because Login.gov's security engineering team was not fully staffed until January 2024. At the conclusion of GAO's review, GSA reported that it had established a data protection policy; however, it has not yet demonstrated that the intended results of implementing this policy are being achieved.
Why GAO Did This Study
The risk of identity theft and fraud has been increasing, and data breaches at federal agencies and in the private sector have resulted in the compromise of millions of Americans' personally identifiable information. The sensitive information obtained in those breaches could be used by malicious actors to commit identity fraud.
GAO was asked to examine how Login.gov compares to commercial solutions. This report, among other things: (1) compares Login.gov's capabilities to selected commercially available solutions; (2) identifies reported agency spending on Login.gov and commercial solutions; and (3) evaluates the extent to which Login.gov and other selected solutions protect the sensitive data they collect and manage.
GAO reviewed the commercial solutions' capabilities and compared them with Login.gov. GAO compared how much agencies spent on commercial solutions and Login.gov. GAO also analyzed and compared Login.gov and commercial vendors' privacy practices with industry best practices.
Recommendations
GAO is making one recommendation to GSA to ensure that Login.gov demonstrates that it fully implemented the policy to test its data backups. GSA concurred with the recommendation.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| General Services Administration | The Administrator of the General Services Administration should direct GSA's Technology Transformation Services division to ensure that Login.gov demonstrates that it fully implemented the policy to test its data backups. |
When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
