Cybersecurity High-Risk Series: Challenges in Securing Federal Systems and Information
Fast Facts
Federal systems are vulnerable to cyberattacks. Our High Risk report identified 10 critical actions for addressing federal cybersecurity challenges.
In this report, the second in a series of four, we cover the 3 actions related to Securing Federal Systems and Information:
- Improve implementation of government-wide cybersecurity initiatives
- Address weaknesses in federal agency information security programs
- Enhance the federal response to cyber incidents to better protect federal systems and information
We've made 712 public recommendations in this area since 2010. Nearly 21% of those recommendations hadn't been implemented as of December 2022.

Highlights
Overview
We have made about 712 recommendations in public reports since 2010 with respect to securing federal systems and information. Until these are fully implemented, federal agencies will be more limited in their ability to protect private and sensitive data entrusted to them. For more information on this report, visit https://www.gao.gov/cybersecurity.
Improve Implementation of Government-Wide Cybersecurity Initiatives
Federal law assigned five key cybersecurity responsibilities to the Cybersecurity and Infrastructure Security Agency (CISA), including securing federal information and systems, and coordinating federal efforts to secure and protect against critical infrastructure risk. To implement these responsibilities, CISA undertook an organizational transformation initiative aimed at unifying the agency, improving mission effectiveness, and enhancing the workplace experience. In March 2021, we reported that CISA had only completed 37 of 94 planned implementation tasks. Critical transformation tasks such as finalizing the mission-essential functions of CISA’s divisions and defining incident management roles and responsibilities across the agency had not yet been completed.
Five Key Responsibilities Assigned to the Cybersecurity and Infrastructure Security Agency
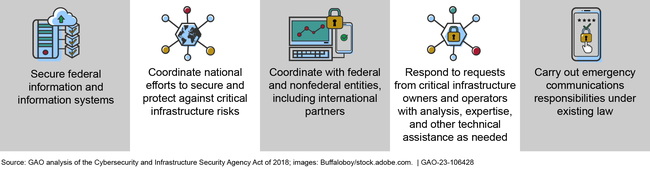
➢ We recommended that CISA establish expected completion dates, plans for developing performance measures, and an overall deadline for the completion of the transformation initiative, as well as develop a strategy for comprehensive workforce planning.
Address Weaknesses in Federal Agency Information Security Programs
To protect federal information and systems, the Federal Information Security Modernization Act of 2014 (FISMA) requires federal agencies to develop, document, and implement information security programs. Congress included a provision in FISMA for GAO to periodically report on agencies’ implementation of the act. In March 2022, we reported on the information security programs of 23 federal civilian agencies, including annually required program reviews to be conducted by agency inspectors general (IG). Among other things, we noted that IGs determined that 16 (or 70 percent) of the 23 agencies had ineffective programs for fiscal year 2020.
Number of the 23 Civilian Agencies with Effective and Not Effective Agency-Wide Information Security Programs, as Reported by Inspectors General for Fiscal Years 2017-2020 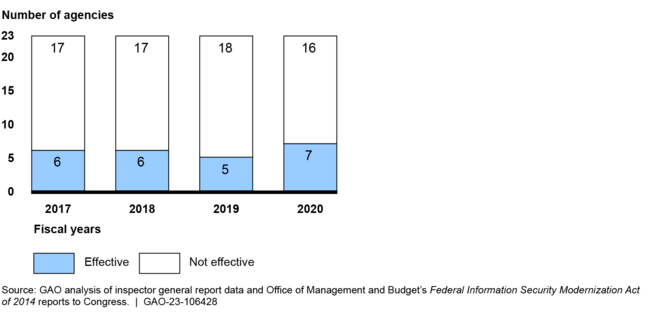
We found that OMB’s guidance to IGs on conducting agency evaluations was not always clear, leading to inconsistent application and reporting by IGs. Further, we reported that the binary effective/not effective scale resulted in imprecise ratings that did not clearly distinguish among the differing levels of agencies’ performance. By clarifying its guidance and enhancing its rating scale, OMB could help ensure more a more consistent approach and nuanced picture of agencies’ cybersecurity programs.
➢ We recommended that OMB, in consultation with others, clarify its guidance to IGs and create a more precise overall rating scale.
Enhance the Federal Response to Cyber Incidents
DOD and our nation's defense industrial base (DIB) are dependent on information systems to carry out their operations. These systems continue to be the target of cyberattacks, as demonstrated by over 12,000 cyber incidents DOD has experienced since 2015.
Cyber Incidents Reported by Department of Defense's Cybersecurity Service Providers from Calendar Years 2015 through 2021
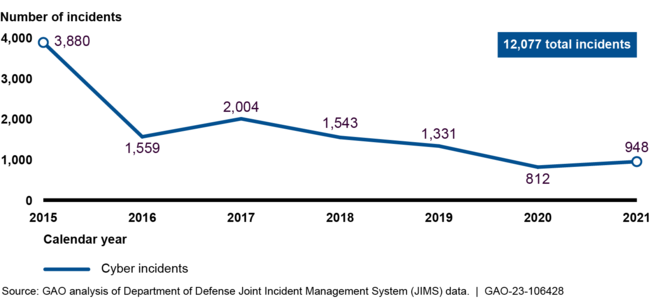
In November 2022, we reported DOD has taken steps to combat these attacks and the number of cyber incidents had declined in recent years. However, we found that the department (1) had not fully implemented its processes for managing cyber incidents, (2) did not have complete data on cyber incidents that staff report, and (3) did not document whether it notifies individuals whose personal data is compromised in a cyber incident.
In addition, according to officials, DOD has not yet decided whether DIB cyber incidents detected by cybersecurity service providers should be shared with all relevant stakeholders. Until DOD examines whether this information should be shared with all relevant parties, opportunities could be lost to identify system threats and improve system weaknesses.
➢ We recommended the Department of Defense improve the sharing of DIB-related cyber incident information and document when affected individuals are notified of a PII breach of their data.
For more information about this Snapshot, contact: Marisol Cruz Cain, Director, Information Technology & Cybersecurity, cruzcainm@gao.gov, (202) 512-5017.
