Business Systems: DOD Needs to Improve Performance Reporting and Cybersecurity and Supply Chain Planning
Fast Facts
The Department of Defense requested about $38.6 billion for FY 2022 for its unclassified information technology, such as communications systems and business systems.
We reviewed the performance of DOD's 25 major IT business programs, management of cybersecurity and supply chain risks, and more. Among other things, we found:
- 19 of the 25 programs did not fully report data measuring progress on system performance
- Programs reported progress on only 77 of 172 performance targets
- 15 of the 25 reported having an approved cybersecurity strategy and provided a copy to validate
Our recommendations address these and other issues.
In FY22, 4 programs accounted for over 50% of DOD’s major IT business systems budget

Highlights
What GAO Found
According to the Department of Defense's (DOD) fiscal year (FY) 2022 submission to the federal IT Dashboard, DOD planned to spend $8.8 billion on its portfolio of 25 major IT business programs between FY 2020 and 2022. In addition, 18 of the 25 programs reported experiencing cost or schedule changes since January 2020. Of these programs, 14 reported the extent to which program costs and schedules had changed, noting cost increases ranging from $0.1 million to $10.7 billion and schedule delays ranging from 5 to 19 months. Program officials attributed the changes to various factors, including requirement changes or delays, contract developments, and technical complexities.
Programs also reported operational performance data to the federal IT Dashboard. As of December 2021, the 25 programs collectively identified 172 operational performance metrics consistent with Office of Management and Budget (OMB) guidance. These metrics covered a range of performance indicators such as the timeliness of program deliverables and the percentage of time that systems were available to users. However, programs only reported progress on 77 of the 172 operational performance targets. (See figure.)
Officials for DOD's 25 Major IT Business Programs Reported Operational Performance Data to the Federal IT Dashboard, as of December 2021
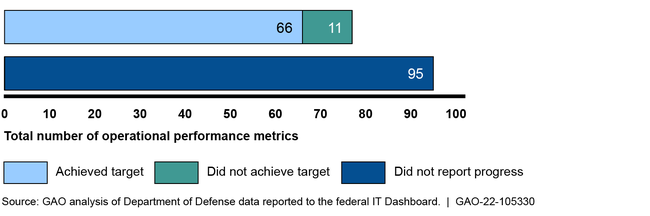
Nineteen programs did not fully report progress on their operational performance. Officials from the Office of the DOD CIO stated that programs that have operational performance measures should be reporting them to the Dashboard. They added that there were multiple factors that could have led to programs not reporting the metrics, including a reorganization that shifted responsibilities for IT investment management and confusion about the reporting requirement. Nevertheless, by reporting incomplete performance data, DOD limits Congress' and the public's understanding of how programs are performing.
As of February 2022, DOD program officials from all 11 (of the 25) major IT business programs that we considered to be actively developing new software functionality reported using recommended iterative development practices that can limit risks of adverse cost and schedule outcomes. Officials from eight of the 11 programs reported using Agile software development, which can support continuous iterative software development. Officials for five of the programs also reported delivering software functionality every 6 months or less, as called for in OMB guidance. Officials for three programs reported a frequency greater than 6 months and officials from the remaining three did not indicate a frequency.
In addition, as of February 2022, officials from the 25 major IT business programs reported on whether they had an approved cybersecurity strategy as required by DOD. (See table.)
Officials for Major DOD IT Business Programs Reported on Whether They Had an Approved Cybersecurity Strategy, as of February 2022
|
Programs' cybersecurity assessment status |
Number of programs |
|
Reported having an approved cybersecurity strategy and provided the strategy |
15 of 25 |
|
Reported having an approved cybersecurity strategy but did not provide the strategy to support their response |
7 of 15 |
|
Reported not having an approved cybersecurity strategy, but planned to develop one |
2 of 25 |
|
Reported not having an approved cybersecurity strategy and did not plan to develop one |
1 of 25 |
Source: GAO analysis of Department of Defense questionnaire responses. | GAO-22-105330
Officials from DOD CIO stated that they will follow up with the programs that did not provide an approved cybersecurity strategy. Until DOD ensures that these programs develop strategies, programs lack assuance that they are effectively positioned to manage cybersecurity risks and mitigate threats.
Officials from the 25 programs also reported on whether they had a system security plan that addresses information and communications technology (ICT) supply chain risk management, as called for by leading practices. (See table.)
Officials for Major DOD IT Business Programs Reported on Whether They Had Information and Communications Technology (ICT) Supply Chain Risk Management Plans, as of February 2022
|
Programs' supply chain risk management plan status |
Number of programs |
|
Reported having a system security plan that addresses ICT supply chain risk management and provided the plan |
10 of 25 |
|
Reported having a system security plan that addresses ICT supply chain risk management, but did not provide the plan to support their response |
1 of 25 |
|
Reported not having a system security plan that addresses ICT supply chain risk management, but planned to develop one |
7 of 25 |
|
Reported not having a system security plan that addresses ICT supply chain risk management and did not plan to develop one |
7 of 25 |
Source: GAO analysis of Department of Defense questionnaire responses. | GAO-22-105330
DOD guidance does not require programs to address ICT supply chain risk management in security plans. According to officials from DOD CIO, IT programs might address supply chain risk management in program protection plans. In addition, they noted that recent supply chain efforts have been focused on weapons systems. However, 15 of DOD's major IT programs did not demonstrate that they had a supply chain risk management plan. Until DOD ensures that these programs have such plans, they are less likely to be able to manage supply chain risks and mitigate threats that could disrupt operations.
Regarding actions to implement legislative and policy changes, the National Defense Authorization Act (NDAA) for FY 2021 eliminated the DOD chief management officer (CMO) position. This position previously had broad oversight responsibilities for DOD business systems. In September 2021, the Deputy Secretary of Defense directed a broad realignment of the responsibilities previously assigned to the CMO. GAO will continue to monitor DOD's efforts to redistribute the roles and responsibilities formerly assigned to the CMO.
Why GAO Did This Study
For fiscal year 2022, DOD requested approximately $38.6 billion for its unclassified IT investments. These investments included programs such as communications and command and control systems. They also included major IT business programs, which are intended to help the department carry out key functions, such as financial management and health care.
The NDAA for FY 2019 included a provision for GAO to assess selected DOD IT programs annually through March 2023. GAO's objectives for this review were to (1) examine how DOD's portfolio of major IT acquisition business programs has performed; (2) determine the extent to which the department has implemented software development, cybersecurity, and supply chain risk management practices; and (3) describe actions DOD has taken to implement legislative and policy changes that could affect its IT acquisitions.
To address these objectives, GAO determined that DOD's major IT business programs were the 25 that DOD reported to the federal IT Dashboard as of December 2021 (The IT Dashboard is a public website that includes information on the performance of IT investments). GAO examined DOD's planned expenditures for these programs from fiscal years 2020 through 2022, as reported in the department's FY 2022 submission to the Dashboard.
GAO obtained the programs' operational performance data from the Dashboard and compared the data to OMB guidance. It also met with DOD CIO officials to determine reasons why programs were not reporting data in accordance with guidance.
In addition, GAO aggregated program office responses to a GAO questionnaire that requested information about cost and schedule changes that the programs experienced since January 2020.
GAO also aggregated DOD program office responses to the questionnaire that requested information about software development, cybersecurity, and supply chain risk management plans and practices. GAO compared the responses to relevant guidance and leading practices.
Further, GAO reviewed actions DOD has taken to implement its plans for addressing previously identified legislative and policy changes that could affect its IT acquisitions. This included reviewing information associated with the department's efforts to (1) finalize strategies for its business system and software acquisition pathways; (2) implement modern approaches to software development such as transitioning to Agile; and (3) reorganize the responsibilities of the former Chief Management Officer throughout the department. GAO met with relevant DOD officials to discuss each of the topics addressed in this report.
Recommendations
GAO is making three recommendations to DOD to ensure programs (1) report operational performance data to the federal IT Dashboard; (2) develop cybersecurity strategies; and (3) develop plans that address ICT supply chain risk management, as appropriate.
DOD concurred with GAO's recommendations and described actions it was taking, and planned to take, to address them.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Defense | The Secretary of Defense should direct the Chief Information Officer to ensure that major IT business programs report operational performance measures, as appropriate, as part of the department's submission to the federal IT Dashboard. (Recommendation 1) |
As of January 2025, DOD has not demonstrated that it has addressed this recommendation. In July 2022, the department stated that DOD was already required to report major investments, including major IT business systems', operational performance metrics to the Federal IT Dashboard per the Office of Management and Budget's A-11 and Capital Planning Guidance. In addition, DOD releases specific IT budget guidance that requires components to report operational metrics for major IT investments. Further, the department indicated that, as a result of the GAO audit finding, DOD implemented an additional audit check to ensure operational performance metrics are provided for all major IT systems and reported to the Federal IT Dashboard. As of April 2024, DOD stated that it has implemented additional audit checks to ensure this occurs; however, we found that six programs had not fully reported performance data on the Dashboard for FY 2024. We will continue to monitor the department's efforts to fully implement this recommendation as part of our next annual review of selected DOD IT programs in 2025.
|
| Department of Defense | The Secretary of Defense should direct the Chief Information Officer to ensure that major IT business programs develop approved cybersecurity strategies, as appropriate. (Recommendation 2) |
As of January 2025, DOD has not demonstrated that it has addressed this recommendation. In July 2022, the department stated that DOD Office of Chief Information Officer (CIO) and the Undersecretary of Defense for Acquisition and Sustainment (USD(A&S)) were working to ensure business programs develop cybersecurity strategies that demonstrate that they are effectively positioned to manage cybersecurity risks and mitigate threats. The department added that the DOD CIO had recently reviewed and approved cybersecurity strategies for several of the major business systems identified in the recommendation. In addition, DOD stated that DOD CIO was updating the cybersecurity strategies' governing guidance. DOD stated that this update will deliver updated cybersecurity guidance to the development, operations, and sustainment of DOD business systems. In September 2023, the department stated that, among other things, DOD CIO, in conjunction with USD(A&S), is continuing to work to ensure business programs develop cybersecurity strategies and indicated that DOD CIO is continuing to review and approve cybersecurity strategies for programs identified in the recommendation. As of March 2024, we found that six programs did not have an approved strategy and DOD CIO officials stated that they were continuing to follow up with the programs to ensure that each develop one. We will continue to monitor the department's efforts to fully implement this recommendation as part of our next annual assessment of selected DOD IT programs in 2025.
|
| Department of Defense | The Secretary of Defense should direct the Chief Information Officer to ensure that major IT business programs develop plans that address information and communication technology supply chain risk management, as appropriate. (Recommendation 3) |
As of January 2025, DOD has not demonstrated that it has addressed this recommendation. In July 2022, the department stated that while components were not required to develop their respective information and communications technology supply chain risk management (ICT-SCRM) policies, DOD had laid the foundation for this National Institute of Standards and Technology Special Publication 800-53 Revision 5 requirement. The department also noted that ICT-SCRM requirements were being added to components' capability planning guidance for fiscal years 2025-29. In addition, the department stated that it was in the process of enhancing Risk Management Framework (RMF) guidance for the SCRM family of controls, tailoring guidance for component implementation. In September 2023, the department stated that, among other things, DOD continues to pursue the strategy to ensure programs are implementing ICT-SCRM through policy and RMF implementation. The department also provided an estimated completion date of December 2024 for addressing this recommendation. However, as of January 2025, DOD has not provided additional information to address this recommendation. We will continue to monitor the department's efforts to fully implement this recommendation.
|
