Defense Cybersecurity: Defense Logistics Agency Needs to Address Risk Management Deficiencies in Inventory Systems
Fast Facts
A Department of Defense task force concluded in 2018 that DOD's inventory management systems were potentially vulnerable to attack. These systems, run by the Defense Logistics Agency, are used to manage the defense supply chain.
We reviewed efforts to reduce the risks in 6 inventory management systems. The agency has taken some prescribed risk management actions but could do more. For example, we found 69% of its plans to fix identified security weaknesses were not carried out on time.
We made 5 recommendations to improve the cybersecurity of these systems.
U.S. cybersecurity has been a topic on our High Risk List since 1997.

Highlights
What GAO Found
For six selected inventory management systems that support processes for procuring, cataloging, distributing, and disposing of materiel, the Defense Logistics Agency (DLA) fully addressed two of the Department of Defense's (DOD) six cybersecurity risk management steps and partially addressed the other four. Specifically, the agency categorized the systems based on risk and established an implementation approach for security controls. However, it only partially addressed the four risk management steps of selecting, assessing, authorizing, and monitoring security controls (see figure).
Extent to Which the Defense Logistics Agency Addressed the Department of Defense's Risk Management Steps for Six Selected Inventory Management Systems
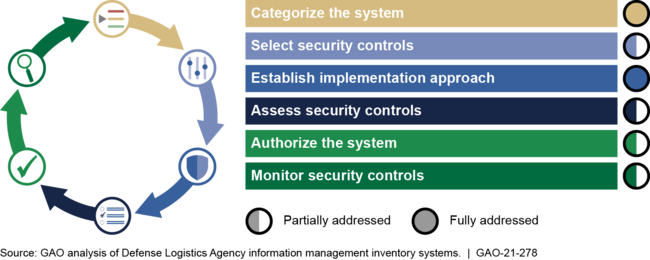
• Select security controls : DLA selected specific security controls, but it did not develop system-level monitoring strategies to assess the effectiveness of selected security controls for three of the six systems GAO assessed. DOD's risk management framework requires components to develop a system-specific monitoring strategy during the security control selection step.
• Assess security controls : DLA assessed the security controls for the six selected inventory management systems, but its assessment procedures lacked approvals, as required. As a result, GAO found that DLA's assessment plans lacked essential details and missed opportunities for risk-based decisions.
• Authorize the system : DLA authorized the selected systems, but it did not report complete and consistent security and risk assessment information to support decisions. GAO found that DLA had not established a process for program offices to review authorization documentation prior to submitting packages to the authorizing official.
• Monitor security controls : DLA did not consistently monitor the remediation of identified security weaknesses across its six inventory management systems. As a result, GAO found that 1,115 of the 1,627 corrective action plans (69 percent) for the six systems did not complete intended remediation within DLA's required time frame of 365 days or less--they were ongoing for an average of 485 days.
Until DLA addresses the identified deficiencies, the agency's management of cyber risks for critical systems will be impeded and potentially pose risks to other DOD systems that could be accessed if DLA's systems are compromised.
Why GAO Did This Study
In November 2018 DOD's Survivable Logistics Task Force examined current and emerging threats to DOD logistics, including cybersecurity threats. The task force concluded that DOD's inventory management systems were potentially vulnerable to cyberattacks, and that DOD did not have corrective action plans to mitigate the potential risks posed by associated vulnerabilities.
House Report 116-120, accompanying a bill for the National Defense Authorization Act for Fiscal Year 2020, included a provision for GAO to evaluate DOD's efforts to manage cybersecurity risks to the DOD supply chain. GAO's report determines the extent to which DLA has implemented risk management steps to address cybersecurity risks to its inventory management systems. GAO selected six systems that DLA officials deemed critical to inventory management operations. GAO reviewed documents, analyzed data, and interviewed officials to determine whether DLA fully addressed, partially addressed, or did not address DOD steps for cybersecurity risk management.
Recommendations
GAO is making five recommendations for DLA to address shortfalls in its critical inventory management systems' adherence to DOD cybersecurity risk management steps. DLA agreed with two and partially agreed with three recommendations. GAO continues to believe all its recommendations are still warranted.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Defense | The Secretary of Defense should ensure that the Director of DLA revises its standard operating procedures to require program offices to develop a system-specific monitoring strategy that is consistent with DOD's risk management framework and related NIST guidance. (Recommendation 1) |
DOD partially concurred with our June 2021 recommendation. In its written comments, DLA stated that the system-level continuous monitoring section of the implementation plan was not initially required by the Enterprise Mission Assurance Support Service (eMASS) system. However, DLA stated that the agency plans to update its Risk Management Framework Standard Operating Procedure by December 31, 2021. DLA updated its SOP to incorporate process improvements and provide additional guidance in March 2022. The SOP now requires each DLA system to document their system level continuous monitoring strategy under the implementation tab in eMASS and align with the enterprise continuous monitoring strategy. According to its corrective action plan, DLA has also taken steps to verify that all DLA systems have provided this entry in eMASS. For example, DLA has incorporated annual verification of system-level continuous monitoring into its validation during annual review and reauthorization submissions. Additionally, eMASS performs automated checks of required fields and produces a yellow warning banner if system-level continuous monitoring fields are incomplete. With these updates, DLA has met the intent of our recommendation and address DOD requirements and related NIST guidance.
|
| Department of Defense | The Secretary of Defense should ensure that the Director of DLA revises and implements an assessment plan approval process that ensures that a designated authorizing official reviews and approves system assessment plans prior to a system being assessed. (Recommendation 2) |
DOD partially concurred with our June 2021 recommendation. In its written comments, DLA stated that assessment plans were not approved by the authorizing official prior to the assessment and validation activities because, while transitioning to the DOD risk management framework, DLA chose to take a more streamlined approach of approving assessment plans during the initial authorization issuance. However, DLA stated the agency plans to update its standard operating procedure by May 1, 2022. In October 2021, the Director of DLA Information Operations issued a memo that identified an Authorizing Official Designated Representative (AODR). The memo designates the AODR responsible for approving security plans and system level continuous monitoring strategy in eMASS. Subsequently, in March 2022, DLA updated its SOP and included a requirement for the Security Plan to be 1) submitted for approval in eMASS using the Security Plan Approval Workflow; and 2) approved prior to the implementation and assessment of the security controls. The approval status will be automatically updated in eMASS to include a status of "approved" and date of AODR's signature. These actions meet the intent of our recommendation.
|
| Department of Defense | The Secretary of Defense should ensure that the Director of DLA directs the DLA Cybersecurity Office to establish a process for program offices to review the consistency and completeness of authorization documentation prior to submitting the package to the designated authorizing officials. (Recommendation 3) |
DOD partially concurred with our June 2021 recommendation. In its written comments, DLA stated that missing items identified during the audit have been added to the corrective action plans in eMASS, and that the agency has a robust approval process for corrective action plans to ensure items are completed properly and thoroughly. According to DLA's March 2022 corrective action plan, the agency has reviewed all of the POA&M items to ensure risk attributes have been completed. In addition, the corrective action plan states that DLA has updated its process to monitor and track corrective actions and will review new actions to ensure risk attributes are complete. DLA has also updated its SOP to reflect this updated process. According to the updated SOP, eMASS will now generate a warning notification for a security authorization package when specific errors exist. Errors could be incomplete system details, missing POA&M information, unassessed security controls or assessment procedures, among other things. These warning notifications can appear as yellow warnings-informational-or red warnings (request cannot proceed forward until the issue has been addressed). These actions meet the intent of our recommendation.
|
| Department of Defense | The Secretary of Defense should ensure that the Director of DLA revises and implements the agency's process for obtaining waivers that accept identified ongoing risk–including the 338 corrective action plans awaiting waivers. (Recommendation 4) |
DOD concurred with our June 2021 recommendation. In its written comments, DLA acknowledged that the approval timeline for its risk waivers were a root cause for the backlog in their remediation of deficiencies. DLA stated that it has successfully implemented an approval process for obtaining waivers. According to its March 2022 SOP, DLA has implemented a revised process to escalate corrective actions that have not been remediated in a timely manner and to manage overdue corrective actions in eMASS. Specifically, DLA requires systems with overdue corrective items be documented and tracked systems in eMASS with a memo to document the rationale describing why the action items were not remediated within the established timeframe as well as a plan for completion to remediate the vulnerabilities on a quarterly basis until the risk associated is reduced below the established risk thresholds. The overdue corrective action workflows are required to be submitted by each system identified As of March 2022, DLA stated it has processed 16 overdue corrective action workflows. These actions meet the intent of our recommendation.
|
| Department of Defense | The Secretary of Defense should ensure that the Director of DLA includes required information—such as residual risk levels—in corrective action plans. (Recommendation 5) |
DOD concurred with our April 2021 recommendation. The department stated that DLA has established a robust POA&M approval process which requires every system to submit new POA&M items for approval on a quarterly basis and to ensure all elements of the POA&M items are completed properly and thoroughly. Additionally, eMASS has made those POA&M elements DLA has established robust required fields that must be filled out when creating new POA&M items. DLA has also ensured that all existing DLA owned ongoing POA&M items have these POA&M fields populated. According to its March 2022 corrective action plan, DLA has reviewed all ongoing correction action items to ensure all risk attribute fields have been properly populated. Specifically, they have reviewed all corrective action items, updated monitoring and tracking efforts, as well as the monthly corrective action reports. These actions meet the intent of our recommendation.
|
