Critical Infrastructure Protection: Actions Needed to Enhance DHS Oversight of Cybersecurity at High-Risk Chemical Facilities
Fast Facts
Terrorists and others may pose a cyber-threat to high-risk chemical facilities. Control systems, for example, could be manipulated to release hazardous chemicals. The Department of Homeland Security started a program more than a decade ago to help address these security risks.
We reviewed the program. DHS guidance designed to help about 3,300 facilities comply with cybersecurity and other standards has not been updated in over 10 years. Also, its cybersecurity training program for its inspectors does not follow some key training practices.
We made 6 recommendations, including that DHS review and update guidance and improve training.

A chemical facility
Highlights
What GAO Found
The Chemical Facility Anti-Terrorism Standards (CFATS) program within the Department of Homeland Security (DHS) evaluates high-risk chemical facilities’ cybersecurity efforts via inspections that include reviewing policies and procedures, interviewing relevant officials, and verifying facilities’ implementation of agreed-upon security measures. GAO found that the CFATS program has guidance designed to help the estimated 3,300 CFATS-covered facilities comply with cybersecurity and other standards, but the guidance has not been updated in more than 10 years, in contrast with internal control standards which recommend periodic review. CFATS officials stated that the program does not have a process to routinely review its cybersecurity guidance to ensure that it is up to date with current threats and technological advances. Without such a process, facilities could be more vulnerable to cyber-related threats.
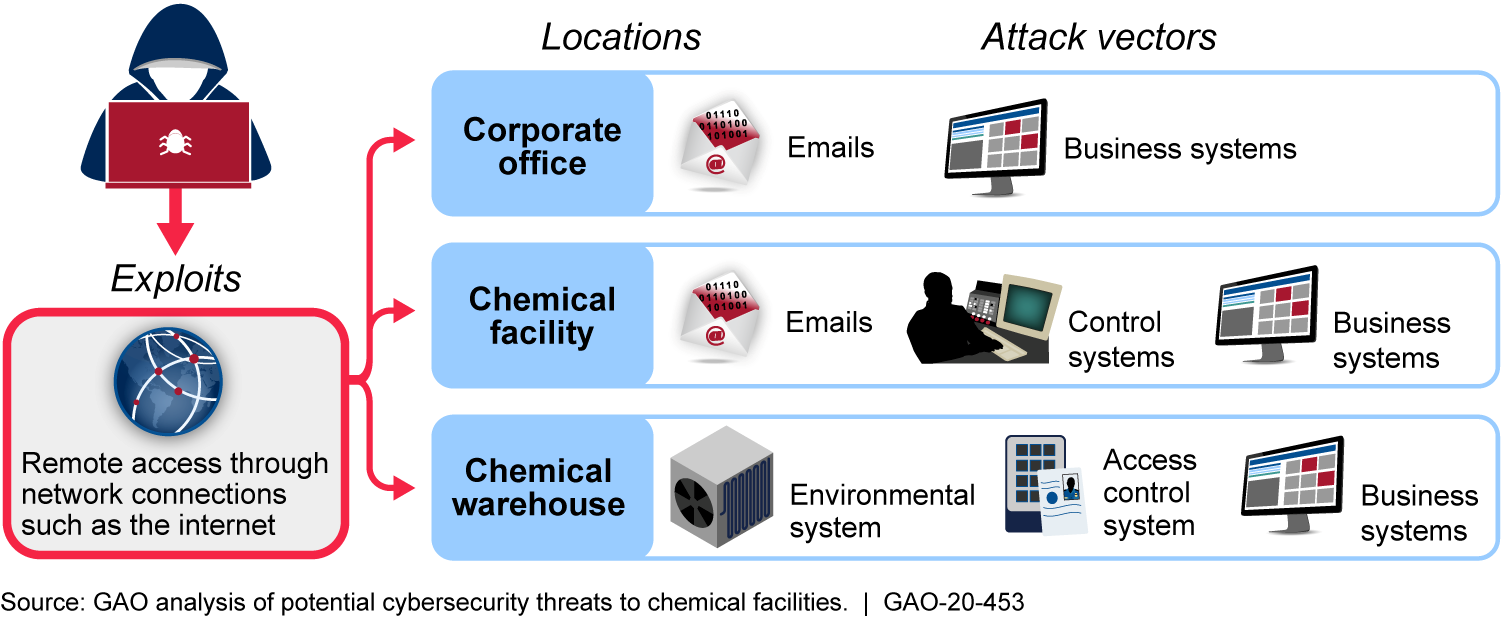
Potential Cyber-Related Threats to Chemical Facilities
The CFATS program developed and provided cybersecurity training for its inspectors, but GAO found that the CFATS program does not fully address 3 of 4 key training practices, or address cybersecurity needs in its workforce planning process, as recommended by DHS guidance. Specifically:
- The CFATS program does not: (1) systematically collect or track data related to inspectors’ cybersecurity training or knowledge, skills, and abilities; (2) develop measures to assess how training is contributing to cybersecurity-related program results; or (3) have a process to evaluate the effectiveness of its cybersecurity training in improving inspector skillsets.
- The program also has yet to incorporate identified cybersecurity knowledge, skills, and abilities for inspectors in its current workforce planning processes or track data related to covered facilities’ reliance on information systems when assessing its workforce needs.
Fully addressing key training practices will help ensure that CFATS inspectors have the knowledge, skills, and abilities for cybersecurity inspections, and identifying cybersecurity needs in workforce planning will help the program ensure that it has the appropriate number of staff to carry out the program’s cybersecurity-related efforts.
Why GAO Did This Study
Thousands of high-risk chemical facilities may be subject to the risk posed by cyber threat adversaries—terrorists, criminals, or nations. These adversaries could potentially manipulate facilities’ information and control systems to release or steal hazardous chemicals and inflict mass causalities to surrounding populations (see figure). In accordance with the DHS Appropriations Act, 2007, DHS established the CFATS program to, among other things, identify and assess the security risk posed to chemical facilities.
GAO was asked to examine the cybersecurity efforts of the CFATS program, including the extent to which the program (1) assesses the cybersecurity efforts of covered facilities, and (2) determines the specialty training and level of staff needed to assess cybersecurity at covered facilities.
GAO conducted site visits to observe the cybersecurity portion of CFATS inspections based on scheduled inspections, reviewed inspection documents, and interviewed CFATS inspectors. GAO also analyzed inspection guidance and training against key practices and assessed workforce planning documents and processes.
Recommendations
GAO is making six recommendations to DHS to routinely review guidance and update, as needed; to fully incorporate key training practices; and to identify workforce cybersecurity needs. DHS concurred with the recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Cybersecurity and Infrastructure Security Agency | The Assistant Director of the Infrastructure Security Division should implement a documented process for reviewing and, if deemed necessary, revising its guidance for implementing cybersecurity measures at regularly defined intervals. (Recommendation 1) |
We found that Chemical Facility Anti-Terrorism Standards (CFATS) program officials had not reviewed or updated the guidance designed to help facilities comply with the cybersecurity and other performance standards for more than 10 years, despite the guidance itself acknowledging the importance of such updates and revisions. CFATS officials also stated that the program did not have a process to routinely review its cybersecurity guidance to ensure that it is up to date with current threats and technological advances. Therefore, we recommended that CISA should implement a documented process for reviewing and, if deemed necessary, revising its guidance for implementing cybersecurity measures at regularly defined intervals. In response, CISA approved an Information Guidance Directive establishing the process by which CISA will review and, as appropriate, update its guidance for implementing cybersecurity measures. The directive includes several notification and review timelines, such as: immediate notification to facilities of any vulnerabilities and threats to their cyber components; quarterly guidance updates to inform facilities on the culmination of important cybersecurity information issued by government and private entities; and long-term reviews of significant guidance, including the CFATS cybersecurity results-based performance standard. These actions are consistent with our recommendation and will help ensure that the CFATS program guidance for cybersecurity better addresses chemical facilities' potential vulnerability to cyberattacks.
|
| Cybersecurity and Infrastructure Security Agency | The Assistant Director of the Infrastructure Security Division should incorporate measures to assess the contribution that its cybersecurity training is making to program goals, such as inspector- or program-specific performance improvement goals. (Recommendation 2) |
DHS concurred with this recommendation. However, on July 28, 2023, the statutory authority for the Chemical Facility Anti-Terrorism Standards (CFATS) program to operate (6 CFR Part 27) expired. Therefore, this recommendation was closed as no longer valid as of January 2025.
|
| Cybersecurity and Infrastructure Security Agency | The Assistant Director of the Infrastructure Security Division should track delivery and performance data for its cybersecurity training, such as the completion of courses, webinars, and refresher trainings. (Recommendation 3) |
DHS concurred with this recommendation. However, on July 28, 2023, the statutory authority for the Chemical Facility Anti-Terrorism Standards (CFATS) program to operate (6 CFR Part 27) expired. Therefore, this recommendation was closed as no longer valid as of January 2025.
|
| Cybersecurity and Infrastructure Security Agency | The Assistant Director of the Infrastructure Security Division should develop a plan to evaluate the effectiveness of its cybersecurity training, such as collecting and analyzing course evaluation forms. (Recommendation 4) |
DHS concurred with this recommendation. However, on July 28, 2023, the statutory authority for the Chemical Facility Anti-Terrorism Standards (CFATS) program to operate (6 CFR Part 27) expired. Therefore, this recommendation was closed as no longer valid as of January 2025.
|
| Cybersecurity and Infrastructure Security Agency |
Priority Rec.
The Assistant Director of the Infrastructure Security Division should develop a workforce plan that addresses the program's cybersecurity-related needs, which should include an analysis of any gaps in the program's capacity and capability to perform its cybersecurity-related functions, and human capital strategies to address them. (Recommendation 5) |
DHS concurred with this recommendation. However, on July 28, 2023, the statutory authority for the Chemical Facility Anti-Terrorism Standards (CFATS) program to operate (6 CFR Part 27) expired. Therefore, this recommendation was closed as no longer valid as of January 2025.
|
| Cybersecurity and Infrastructure Security Agency | The Assistant Director of the Infrastructure Security Division should maintain reliable, readily available information about the cyber integration levels of covered chemical facilities and inspector cybersecurity expertise. This could include updating the program's inspection database system to better track facilities' cyber integration levels. (Recommendation 6) |
DHS concurred with this recommendation. However, on July 28, 2023, the statutory authority for the Chemical Facility Anti-Terrorism Standards (CFATS) program to operate (6 CFR Part 27) expired. Therefore, this recommendation was closed as no longer valid as of January 2025.
|
