Personnel Vetting: DOD Needs to Enhance Cybersecurity of Background Investigation Systems
Fast Facts
DOD's Defense Counterintelligence and Security Agency conducts background investigation operations for most federal agencies.
It does so through a combination of old IT systems previously owned by the Office of Personnel Management, and the new, not-fully-developed National Background Investigation Services IT system.
However, the agency hasn't fully followed DOD's planning steps for cybersecurity risk management, or fully implemented privacy controls for any of the IT systems involved.
We recommended, among other things, that DOD establish oversight processes to help ensure its IT systems are protected.

Highlights
What GAO Found
To conduct background investigations, the Department of Defense's (DOD) Defense Counterintelligence and Security Agency (DCSA) currently uses a combination of recently developed DOD National Background Investigation Services systems and legacy systems formerly owned by the Office of Personnel Management (OPM). In considering the cybersecurity risks of these systems, DCSA did not fully address all planning steps of DOD's risk management framework (see figure).
Extent to Which Defense Counterintelligence and Security Agency Addressed DOD's Planning-Related Risk Management Steps for Selected Background Investigation Systems as of December 2023 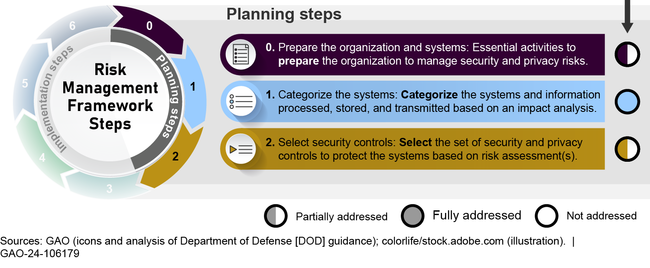
Note: DOD's implementation-related Risk Management Steps are to (3) establish an implementation approach, (4) assess security controls, (5) authorize the systems, and (6) monitor security controls.
- Prepare the organization and systems: Of the 16 tasks required by this step in DOD's risk management framework, DCSA fully addressed 11, partially addressed two, and did not address three. For example, the agency has not fully defined and prioritized security and privacy requirements, nor has it performed organizational and system-level risk assessments.
- Categorize the systems: DCSA appropriately categorized the six reviewed systems as high impact risks .
- Select security controls: DCSA selected baseline security controls for the six systems but used an outdated version of government-wide guidance as the source for the control selections. Specifically, version five of applicable National Institute for Standards and Technology guidance was issued in 2020. However, DCSA continues to use version four. Among the changes in version five are two new categories of controls on personally identifiable information and supply chain management, raising the number of control categories from 18 to 20.
Regarding privacy, DCSA partially implemented controls on developing policies and procedures, delivering training, defining and reviewing the types of events to log, and assessing controls and risks. The agency lacks an oversight process to help ensure that appropriate privacy controls are fully implemented. Until DCSA establishes such an oversight process and fully implements privacy controls, it unnecessarily increases the risks of disclosure, alteration, or loss of sensitive information on its background investigation systems.
Why GAO Did This Study
In the wake of a 2015 OPM breach that compromised sensitive data on over 22 million federal employees and contractors, DCSA later assumed responsibility for conducting background investigation operations for most executive branch agencies.
House Report 117-118 includes a provision for GAO to evaluate the cybersecurity of DCSA's background investigation systems. GAO assessed the extent to which DCSA (1) planned for cybersecurity controls for selected background investigation systems and (2) implemented privacy controls for these systems.
GAO selected three DCSA systems and three OPM legacy systems critical to background investigation operations. GAO (1) reviewed policies, processes, and documentation for these systems and (2) interviewed agency officials regarding the planning and management of cybersecurity risks and selected privacy controls. GAO also has ongoing work assessing DCSA's implementation of technical controls for background investigation systems. It will be published in a future report with limited distribution.
Recommendations
GAO is making a total of 13 recommendations to DOD on fully implementing risk management planning steps, selecting appropriate security controls using current guidance, fully implementing privacy controls, and establishing oversight processes to help ensure required tasks and controls are implemented. DOD concurred with 12 of 13 recommendations and non-concurred with one. GAO maintains that all recommendations are warranted.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer identifies and documents all stages of the information life cycle for each information type the system processes, stores, or transmits. (Recommendation 1) |
DOD agreed with this recommendation with comment. DCSA has taken steps to identify and document all stages of the information life cycle for each information type the system processes, stores, or transmits. Specifically, in August 2024, DCSA's Chief Information Security Officer analyzed the Categorization Level Agreements (CLAs) of select DCSA systems to ensure compliance with Department of Defense Instruction 8510.01 - Risk Management Framework and related processes and instructions. This review focused on the categorization steps and identified gaps in the CLA documents for the select NBIS and legacy systems. Additionally, the CISO tasked system owners to review the CLA pertinent to their systems for accuracy, update as required, route for stakeholder signature, upload to Enterprise Mission Assurance Support Service (eMASS), and submit proof of fully signed CLA by September 5, 2024. In fiscal year 2025, we verified that CLA documents for the select NBIS and legacy systems were complete (i.e., identified any information life cycles) and approved. These actions help DCSA identify considerations for protecting the information, informs its security and privacy risk assessments, and inform the selection and implementation of security and privacy controls.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer fully defines, prioritizes, and documents security and privacy requirements. (Recommendation 2) |
DOD agreed with this recommendation. In fiscal year 2024, DCSA updated the privacy impact assessments (PIA) for the six select systems to address the deficiencies we identified in our original assessment. Specifically, the PIAs identified privacy requirements were applicable and included required signatures. This action helps ensure DCSA completes all requirement definition tasks in the prepare step of the Department of Defense's Risk Management Framework.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer completes an organization-wide risk assessment and documents the results. (Recommendation 3) |
DOD agreed with this recommendation, with comment. In fiscal year 2024, DCSA established a process to provide a monthly status update on DCSA IT systems-including NBIS and legacy systems. The update includes authorization information, status of POA&Ms, progress in the RMF, and FISMA compliance status by system. This action helps ensure DCSA makes an informed determination of risks.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer completes system-level risk assessments and documents the results. (Recommendation 4) |
DOD agreed with this recommendation, with comment. In Fiscal Year 2025, DCSA provided risk assessment reports as evidence of system level risk assessments for the six select NBIS systems, including the three legacy systems (eQIP, OPIS, and PIPS). These assessments will better position DCSA's CIO to fully address essential preparation activities needed to manage cybersecurity risks, such as providing context and setting priorities for privacy and security.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer allocates security and privacy requirements to the system and to the environment in which the system operates and documents the results. (Recommendation 5) |
DOD agreed with this recommendation, with comment. In Fiscal Year 2025, DCSA identified the security and privacy requirements for the six selected NBIS systems. These requirements are documented as common controls in their automated system of record eMASS. DCSA's actions support the agency's efforts to address essential preparation activities needed to manage cybersecurity risks, such as providing context and setting priorities for privacy and security.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer establishes an oversight process to ensure senior officials complete all tasks in the risk management framework's prepare step. (Recommendation 6) |
DOD agreed with this recommendation, with comment. According to a June 2024 DCSA Executive Order, issued in response our report and third-party assessment, the agency has integrated the governance structure of DCSA's CIO and CISO to fully integrate oversight of the NBIS program. The order included oversight and governance measures designed to ensure that its systems and data remain secure, including oversight parameters and risk objective scores. Additionally, DCSA has taken actions to implement our other recommendations (i.e., recommendations 1-5) that support their efforts to address essential preparation activities needed to manage cybersecurity risks, such as providing context and setting priorities for privacy and security.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer updates the selected security control baselines for NBIS and legacy systems to correspond with the current version of NIST Special Publication 800-53 after DOD updates the relevant guidance. (Recommendation 7) |
DOD agreed with this recommendation, with comment. In Fiscal Year 2025, DSCA updated the selected security controls for the six select NBIS systems to be consistent with current NIST guidance and documented this transition in eMASS. DCSA's CIO provided an authorization decision approving this transition of DCSA's Common Controls to NIST SP 800-53 Rev 5 to be consistent with current NIST guidance. As a result, DCSA can have reasonable assurance that the agency has the minimum protection necessary to effectively manage security risks and the six select systems.
|
| Department of Defense | The Secretary of Defense should ensure DOD's Chief Information Officer updates the department's policies and procedures related to the Risk Management Framework to use the current version of NIST Special Publication 800-53. (Recommendation 8) |
DOD did not agree with this recommendation; however, we believed the recommendation was warranted. DOD issued a memo in October 2023 announcing the department's adoption and transition timeline to NIST Special Publication 800-53 Revision 5. According to the memo, systems that have a current authorization decision should develop a strategy and schedule for the transition that must not exceed the system re-authorization timeline of every three years. The six background investigation systems we selected each received approval or authorization to operate on the DOD network between July 2023 and November 2023. Thus, these six systems would need to establish strategies and schedules within three years of their authorization dates. DSCA CISO issued a memo for its Agency IT System Program Managers that documented its strategy and schedule for implementing these additional controls and stated that IT systems that have a current (within 3 years) RMF system authorization decision should continue under Revision 4 and develop a strategy and schedule for transition to Revision 5 submitted for the Authorizing Official's (AO's) approval by April 30, 2025. In Fiscal Year 2025, DSCA migrated the common controls for the six select NBIS systems to be consistent with current NIST guidance and documented this transition in eMASS. These actions provide reasonable assurance that DCSA will have the minimum protection necessary to effectively manage security risks of the six background investigation systems.
|
| Department of Defense | The Secretary of Defense should direct DCSA's Chief Information Officer to ensure the agency's policies and procedures include key information and are reviewed and updated as required. (Recommendation 9) |
DOD agreed with this recommendation, with comment. In its written comments, DCSA described plans to update its policies and procedures by October 2024. In Fiscal Year 2025, DCSA provided evidence that the policies and procedures for the selected privacy controls include key information and have evidence of review or updates, as required. As a result of these actions, DCSA management will be better positioned to ensure continued effectiveness in achieving the agency's objectives.
|
| Department of Defense | The Secretary of Defense should direct DCSA's Chief Information Officer to ensure all security training and certifications for its system users are current. (Recommendation 10) |
DOD agreed with this recommendation, with comment. In Fiscal Year 2025, DCSA took actions to ensure all security training and certifications for its system users are current. The agency stated they have begun using a single tool to track compliance with certification and other DOD requirements for NBIS privileged users. This tool includes management oversight of required annual cybersecurity awareness training to teach personnel about various types of security threats and how best to protect against them. This tool also allows DCSA to manage user compliance and notifies users via email of upcoming due dates, including any past due.
|
| Department of Defense | The Secretary of Defense should direct DCSA's Chief Information Officer to ensure the agency establishes a rationale for why the selected event types can support incident investigations and defines a frequency for reviewing and updating which types of events are to be logged. (Recommendation 11) |
DOD agreed with this recommendation, with comment. In Fiscal Year 2025, DCSA provided evidence of its Cyber Incident Response Process. This process outlines steps taken to include incident detection/identification, triage, containment, eradication, recovery/restoration, post-incident activities, and after actions. Additionally, DCSA provided their Cybersecurity Incident Response Plan. This plan outlines the process for responding to cybersecurity incidents, defines the roles and responsibilities of participants, describes the processes and procedures used to protect the Information Systems, data, and personnel, and establish the guidelines for reporting cybersecurity incidents. As a result of these actions, DCSA has increased assurance that the agency is logging all events necessary to support the investigation of incidents.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure that control assessment plans are documented and that assessments align with these plans. (Recommendation 12) |
DOD agreed with this recommendation, with comment. DCSA program management officers for the six selected NBIS systems submitted controls assessments for review and approval in August 2024. These plans identify the methods used for conducting an assessment of security within the assessment and authorization boundary. They also describe the manner in which results are to be documented and presented during and after the assessment. Lastly, the plans include a description of automated and manual vulnerability assessment tools and assigns responsibilities for the assessment. As a result of these actions, DCSA senior officials and support risk responses will be better informed of relevant threats, vulnerabilities, and impact to the organization as well as the likelihood that harm will occur.
|
| Department of Defense | The Secretary of Defense, in coordination with the DCSA Director, should ensure DCSA's Chief Information Officer establishes an oversight process to ensure senior DCSA officials fully implement the recommended tasks for the required privacy controls. (Recommendation 13) |
DOD agreed with this recommendation, with comment. In fiscal year 2024, DCSA established a process to provide a monthly status update on DCSA IT systems-including NBIS and legacy systems. Additionally, DCSA developed a risk evaluation process to evaluate the overall cybersecurity risk posture, among other things. Lastly, DCSA updated the appointments of personnel assigned to the roles of Information System Owner (ISO). The ISO's primary responsibility is to implement the RMF and execute all RMF activities, among other things. These actions help ensure senior DCSA officials fully implement all recommended tasks to include those for privacy controls.
|
