Cybersecurity High-Risk Series: Challenges in Protecting Privacy and Sensitive Data
Fast Facts
Federal systems are vulnerable to cyberattacks. Our High Risk report identified 10 critical actions for addressing federal cybersecurity challenges.
In this report, the last in a series of four, we cover the 2 actions related to Protecting Privacy and Sensitive Data:
- Improve federal efforts to protect privacy and sensitive data, such as reducing the cybersecurity risks in retirement plans
- Improve the protection of federally collected and maintained personal and sensitive data
We've made 236 public recommendations in this area since 2010. Nearly 60% of those recommendations had not been implemented as of December 2022.

Highlights
Overview
We have made 236 recommendations in public reports since 2010 with respect to protecting cyber critical infrastructure. Until these are fully implemented, federal agencies will be more limited in their ability to protect private and sensitive data entrusted to them. For more information on this report, visit https://www.gao.gov/cybersecurity.
Improve Federal Efforts to Protect Privacy and Sensitive Data
In September 2022, our review of 24 agencies found that most had generally established policies and procedures for key privacy program activities. These activities included, among other things, developing system-of-records notices that identify types of personal data collected, conducting privacy impact assessments, and documenting privacy program plans. Agencies varied in establishing policies and procedures for coordinating privacy programs with other agency functions. Further, many agencies did not fully incorporate privacy into their risk management strategies, provide for privacy officials’ input into the authorization of systems containing PII, or develop a continuous monitoring strategy for privacy. Without fully establishing these elements of their privacy programs, agencies have less assurance that they are consistently implementing privacy protections.
Extent to Which 24 Chief Financial Officers Act of 1990 Agencies Addressed Key Practices for Establishing a Privacy Program
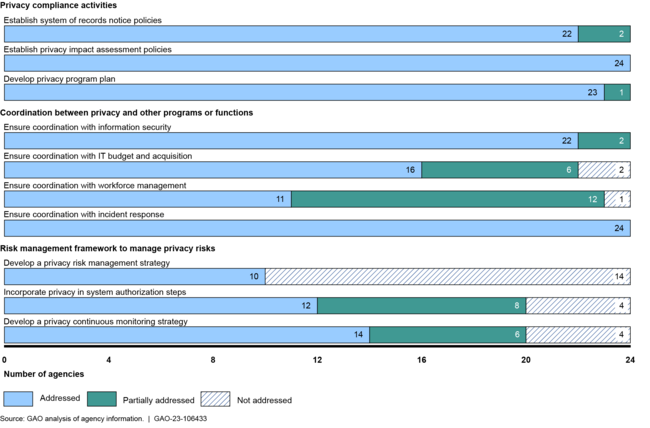
➢ We recommended that Congress consider legislation to designate a dedicated, senior-level privacy official at agencies that lacked one. We also made recommendations to the Office of Management and Budget to facilitate information sharing to help agencies address selected challenges and better implement privacy impact assessments. Finally, we made recommendations to 23 of the 24 agencies we reviewed to fully implement all of the key practices for their privacy programs.
Appropriately Limit the Collection and Use of Personal Information and Ensure that it is Obtained with Appropriate Knowledge or Consent
In June 2021, we reported on the results of our survey of 42 federal agencies that employ law enforcement officers about their use of facial recognition technology. Twenty reported owning systems with facial recognition technology or using systems owned by other entities, such as other federal, tribal, state, local, and territorial governments and non-government entities.
Types of Photos Used by Federal Agencies That Employ Law Enforcement Officers

Agencies reported using the technology to support several activities (e.g., criminal investigations) and in response to COVID-19 (e.g., to verify an individual’s identity remotely). All 14 agencies that we reviewed reported using the technology to support criminal investigations also reported using systems owned by non-federal entities. However, only one of those 14 was aware of what non-federal systems employees used. By having a mechanism to track what non-federal systems employees use and assessing privacy and accuracy-related risks, agencies can better mitigate risks to themselves and the public.
➢ We recommended that 13 federal agencies implement a mechanism to track what non-federal systems with facial recognition technology employees use and assess the risks of using these systems.
In January 2022, we reported that the five federal financial regulators we reviewed had built more than 100 information system applications that regularly collect and use extensive amounts of PII to fulfill their regulatory missions. These regulators collect PII directly from individuals and financial institutions and share it with entities such as banks or service providers, contractors and other third parties, and other federal and state regulators. Regulators use the PII to conduct supervisory examinations of financial institutions and to receive and respond to complaints or inquiries from customers.
Collection, Use, and Sharing of Personally Identifiable Information (PII) at Selected Federal Financial Regulators
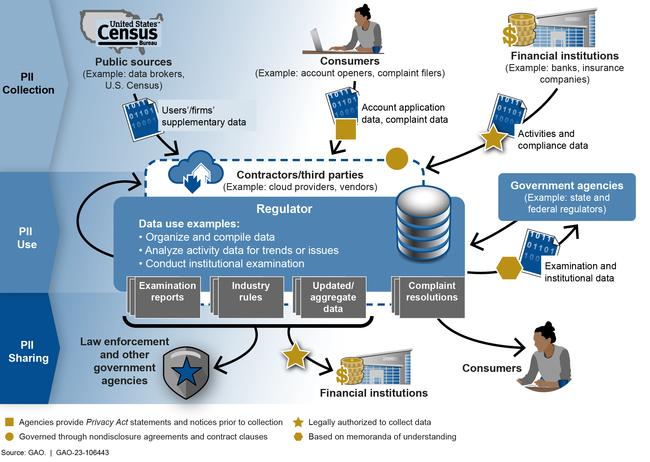
We reported that the financial regulators we reviewed created privacy programs that generally take steps to protect PII in accordance with key practices in federal guidance. However, four of the regulators did not fully implement key practices in other privacy protection areas. For example, these regulators did not document steps taken to minimize the collection and use of PII. Until these regulators take steps to mitigate these weaknesses, the PII they collect, use, and share could be at increased risk of compromise.
➢ We made several recommendations that federal financial regulators better ensure the privacy of the PII that they collect, use, and share.
For more information about this Snapshot, contact: Marisol Cruz Cain, Director, Information Technology & Cybersecurity, cruzcainm@gao.gov, (202) 512-5017.
