Cybersecurity: Selected Federal Agencies Need to Coordinate on Requirements and Assessments of States
Fast Facts
States must follow numerous cybersecurity requirements when using federal data. These requirements may vary by federal agency.
State information security officials we surveyed told us, among other things, that the differing requirements cost states additional time and money, and could ultimately detract from security efforts.
Among the 4 federal agencies we examined, 49% to 79% of security requirement parameters—the number of log-on attempts allowed, for example—were in conflict.
We made 12 recommendations, including that the Office of Management and Budget improve coordination of cybersecurity requirements among federal agencies.

Lock and keyboard
Highlights
What GAO Found
Although the Centers for Medicare and Medicaid Services (CMS), Federal Bureau of Investigation (FBI), Internal Revenue Service (IRS), and Social Security Administration (SSA) each established requirements to secure data that states receive, these requirements often had conflicting parameters. Such parameters involve agencies defining specific values like the number of consecutive unsuccessful logon attempts prior to locking out the user. Among the four federal agencies, the percentage of total requirements with conflicting parameters ranged from 49 percent to 79 percent. Regarding variance with National Institute of Standards and Technology guidance, GAO found that the extent to which the four agencies did not fully address guidance varied from 9 percent to 53 percent of total requirements. The variances were due in part to the federal agencies' insufficient coordination in establishing requirements. Although the Office of Management and Budget's (OMB) Circular A-130 requires agencies to coordinate, OMB has not ensured that agencies have done so. Further, while federal agencies' variance among requirements may be justified in some cases because of particular agency mission needs, the resulting impact on states is significant, according to state chief information security officers (see figure).
Extent of Impacts Identified by State Chief Information Security Officers as a Result of Variances in Selected Federal Agencies' Cybersecurity Requirements
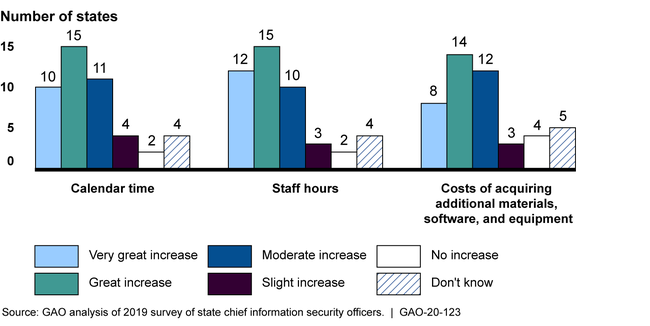
Note: Not all respondents answered all survey questions. The figure is based on 46 responses.
The four federal agencies that GAO reviewed either fully or partially had policies for coordinating assessments with states, but none of them had policies for coordinating assessments with each other. State chief information security officers that GAO surveyed reinforced the need to coordinate assessments by identifying impacts on state agencies' costs, including multiple federal agencies that requested the same documentation. Coordinating with state and federal agencies when assessing state agencies' cybersecurity may help to minimize states' cost and time impacts and reduce associated federal costs. Federal agencies reported spending about $45 million for fiscal years 2016 through 2018 on assessments of state agencies' cybersecurity.
Why GAO Did This Study
To protect data that are shared with state government agencies, federal agencies have established cybersecurity requirements and related compliance assessment programs. Specifically, they have numerous cybersecurity requirements for states to follow when accessing, storing, and transmitting federal data.
GAO was asked to evaluate federal agencies' cybersecurity requirements and related assessment programs for state agencies. The objectives were to determine the extent to which (1) selected federal agencies' cybersecurity requirements for state agencies varied with each other and federal guidance, and (2) federal agencies had policies for coordinating their assessments of state agencies' cybersecurity.
GAO reviewed four federal agencies that shared data with states and had assessment programs: CMS, FBI, IRS, and SSA. GAO compared, among other things, each agency's cybersecurity requirements to federal guidance and to other selected agencies' requirements; and reviewed federal agencies' policies for conducting assessments. In addition, GAO examined OMB's efforts to foster coordination among federal agencies. GAO also surveyed and received responses from chief information security officers in 50 out of 55 U.S. states, territories, and the District of Columbia to obtain their perspectives.
Recommendations
GAO is making 12 recommendations to the four selected agencies and to OMB. Three agencies agreed with the recommendations and one agency (IRS) partially agreed or disagreed with them. OMB did not provide comments. GAO continues to believe all recommendations are warranted.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Office of Management and Budget |
Priority Rec.
The Director of OMB should ensure that CMS, FBI, IRS, and SSA are collaborating on their cybersecurity requirements pertaining to state agencies to the greatest extent possible and direct further coordination where needed. (Recommendation 1) |
While OMB did not agree or disagree with GAO's recommendation, the Administration has taken steps that address our recommendation. Since we issued our report in May 2020, Congress established the Office of the National Cyber Director (ONCD)-a component of the Executive Office of the President-to advise the President of the United States on cybersecurity policy and strategy. In August 2023, ONCD issued a request for information seeking input on challenges with cybersecurity regulatory overlap and received over 100 public comments. In its June 2024 summary of the public comments, ONCD highlighted comments identifying a need for greater regulatory harmonization between federal agencies and State, Local, Tribal, and Territorial governments. ONCD stated that it established a reciprocity pilot program pursuant to the National Cybersecurity Strategy Implementation Plan Version 2.0 that is to surface insights on how to achieve reciprocity among various cybersecurity regulations. Further, in April 2024 the Administration released National Security Memorandum-22 on Critical Infrastructure Security and Resilience. The memorandum calls for federal agencies with regulatory authorities to establish minimum requirements and effective accountability mechanisms for the security and resilience of critical infrastructure, which includes State, Local, Tribal, and Territorial governments. Federal agencies are also to harmonize these efforts to the maximum extent possible through participation in federal interagency working groups. ONCD, in coordination with OMB, is to lead the federal government's cybersecurity regulation harmonization efforts. By encouraging federal agencies to collaborate to make their cybersecurity requirements for state agencies consistent to the greatest extent possible, the federal government is less likely to create additional fragmentation of cybersecurity policies for states.
|
| Office of Management and Budget |
Priority Rec.
The Director of OMB should take steps to ensure that CMS, FBI, IRS, and SSA coordinate, where feasible, on assessments of state agencies' cybersecurity, which may include steps such as leveraging other agencies' security assessments or conducting assessments jointly. (Recommendation 2) |
While OMB did not agree or disagree with GAO's recommendation, the Administration has taken steps that address our recommendation. Since we issued our report in May 2020, Congress established the Office of the National Cyber Director (ONCD)-a component of the Executive Office of the President-to advise the President of the United States on cybersecurity policy and strategy. In August 2023, ONCD issued a request for information seeking input on challenges with cybersecurity regulatory overlap and received over 100 public comments. In its June 2024 summary of the public comments, ONCD highlighted comments identifying a need for greater regulatory harmonization between federal agencies and State, Local, Tribal, and Territorial governments. ONCD stated that it established a reciprocity pilot program pursuant to the National Cybersecurity Strategy Implementation Plan Version 2.0 that is to surface insights on how to achieve reciprocity among various cybersecurity regulations. Further, in April 2024 the Administration released National Security Memorandum-22 on Critical Infrastructure Security and Resilience. The memorandum calls for federal agencies with regulatory authorities to establish minimum requirements and effective accountability mechanisms for the security and resilience of critical infrastructure, which includes State, Local, Tribal, and Territorial governments. Federal agencies are also to harmonize these efforts to the maximum extent possible through participation in federal interagency working groups. ONCD, in coordination with OMB, is to lead the federal government's cybersecurity regulation harmonization efforts. By encouraging federal agencies to collaborate on accountability mechanisms, such as assessments, the federal agencies are more likely to leverage compatible cybersecurity assessments and reduce fragmented assessments among state agencies.
|
| Centers for Medicare & Medicaid Services | The Administrator of CMS should, in collaboration with OMB, solicit input from FBI, IRS, SSA, and state agency stakeholders on revisions to its security policy to ensure that cybersecurity requirements for state agencies are consistent with other federal agencies and NIST guidance to the greatest extent possible and document CMS's rationale for maintaining any requirements variances.(Recommendation 3) |
CMS agreed with and has taken steps to implement this recommendation. CMS has participated in the FBI's Criminal Justice Information Services Division Modernization Task Force, which includes representatives from the FBI and Internal Revenue Service, to discuss the impact of inconsistent cybersecurity standards. Further, CMS revised its security assessment policy in April 2025 to improve coordination with other federal agencies. CMS also updated its state cybersecurity requirements policy-named the Acceptable Risk Controls for ACA, Medicaid, and Partner Entities-to align security controls with guidance from NIST Special Publication 800-53 and other federal agencies. CMS stated that it solicited feedback from federal agency partners prior to publishing the policy. However, as of February 2026 CMS has not provided supporting documentation on its efforts to solicit and incorporate this feedback. To fully address this action, CMS needs to demonstrate efforts it has taken to solicit input from state and federal agency stakeholders on updates to its state cybersecurity requirements policy. We will continue to monitor the agency's progress in implementing this recommendation.
|
| Centers for Medicare & Medicaid Services |
Priority Rec.
The Administrator of CMS should revise its assessment policies to maximize coordination with other federal agencies to the greatest extent practicable. (Recommendation 4) |
CMS agreed with and has taken steps to implement our recommendation. In February 2025, CMS provided its security assessment policy, which it revised in June 2022. CMS's policy identifies multiple options for meeting the requirements of an independent assessment, including leveraging other assessments that address MARS-E requirements. Allowing audited entities to leverage other assessment results and related documentation, which could include assessments from another federal agency that reviewed the same information resources, further enhances coordination between CMS and other federal agencies. By taking these steps, CMS may reduce unnecessary burdens on state officials' time and resources in responding to duplicative requests and inquiries, retesting controls that have already been evaluated, or reporting similar findings.
|
| Federal Bureau of Investigation |
Priority Rec.
The FBI Director should, in collaboration with OMB, solicit input from CMS, IRS, SSA, and state agency stakeholders on revisions to its security policy to ensure that cybersecurity requirements for state agencies are consistent with other federal agencies and NIST guidance to the greatest extent possible. (Recommendation 5) |
FBI agreed with and has taken steps to implement this recommendation. As of February 2024, FBI revised its security policy to further align with security control guidance from the National Institute of Standards and Technology (NIST) and based on input from federal and state agencies. In September 2023, it released its updated Criminal Justice Information Services (CJIS) Security Policy to further align security controls with guidance from NIST Special Publication 800-53. As a result, FBI has addressed a large amount of the variances with other federal agencies' requirements that GAO originally identified. Subsequently, FBI has continued to hold CJIS Policy Modernization Task Force meetings, consisting of representatives from the CMS, IRS, and SSA as well as IT representatives from state law enforcement agencies and courts, to advise FBI on updates to its cybersecurity requirements. By taking these steps, FBI potentially reduced unnecessary burdens on state officials' time and resources in responding to variances from multiple federal agencies' cybersecurity requirements.
|
| Federal Bureau of Investigation | The FBI Director should fully develop policies for coordinating with state agencies on the use of prior findings from relevant cybersecurity assessments conducted by other organizations. (Recommendation 6) |
As of November 2020, FBI's Criminal Justice Information Services (CJIS) Division updated its policies for cybersecurity assessments to include use of prior findings from relevant assessments conducted by other organizations. For example, FBI's CJIS Division updated its Information Technology Security Audit Training Manual and Information Technology Security Audit CJIS System Pre-audit Questionnaire to include the review of previous third-party audit findings as part of the audit planning process. By implementing this recommendation, FBI may potentially reduce unnecessary burdens on state officials' time and resources in responding to overlapping or duplicative requests and inquiries, reviewing controls that have already been evaluated, or reporting similar findings multiple times throughout a state.
|
| Federal Bureau of Investigation |
Priority Rec.
The FBI Director should revise its assessment policies to maximize coordination with other federal agencies to the greatest extent practicable. (Recommendation 7) |
FBI agreed with and has taken steps to implement this recommendation. As of February 2023, FBI's Criminal Justice Information Services (CJIS) Audit Unit held discussions with officials from CMS, IRS, and SSA to share information on the assessment processes for state agencies, such as what agencies and data are included in assessments, previous assessment results, and the potential for further coordination of assessment schedules. FBI noted that it expects to continue to hold these discussions biannually. Further, FBI revised its assessment procedures to include a step for reviewing third-party audit results-such as those from CMS, IRS, and SSA, or others-and incorporating those results into FBI's assessment plans. By taking these steps, FBI may reduce unnecessary burdens on state officials' time and resources in responding to duplicative requests and inquiries, retesting controls that have already been evaluated, or reporting similar findings.
|
| Internal Revenue Service | The IRS Commissioner should, in collaboration with OMB, solicit input from CMS, FBI, SSA, and state agency stakeholders on revisions to its security policy to ensure that cybersecurity requirements for state agencies are consistent with other federal agencies and NIST guidance to the greatest extent possible. (Recommendation 8) |
As of December 2021, IRS revised its security policy based on new guidance from the National Institute of Standards and Technology (NIST) and input from federal and state agencies to implement GAO's May 2020 recommendation. The agency completed a comparison of IRS Publication 1075 with NIST Special Publication 800-53, Revision 5 to identify areas where its security policy could be more consistent with NIST. In addition, IRS participated in discussions with officials from the CMS, FBI, and SSA to discuss the impact of inconsistent cybersecurity standards among the agencies. In addition, IRS sent a draft of its update on Publication 1075 to federal and state agencies, and incorporated their comments in the final version of the publication that was released in December 2021. By implementing this recommendation, IRS potentially reduced unnecessary burdens on state officials' time and resources in responding to variances from multiple federal agencies' cybersecurity requirements.
|
| Internal Revenue Service | The IRS Commissioner should revise its assessment policies to maximize coordination with other federal agencies to the greatest extent practicable. (Recommendation 9) |
As of December 2021, IRS incorporated federal agency coordination into its assessments of state agencies' cybersecurity to implement GAO's May 2020 recommendation. IRS shared its fiscal year 2021 agency review schedule with CMS, FBI, and SSA in an effort to coordinate and reduce unnecessary burden to state agencies. Further, in preparing for its fiscal year 2021 assessments, IRS solicited results from assessments conducted by other federal agencies that may cover the same technologies in the scope of the IRS assessment. IRS has also incorporated the above coordination steps into its planning procedures for state agency assessments. IRS's planning procedures now include steps for determining whether the agency can use results from another federal assessment in lieu of a full assessment by IRS. By implementing this recommendation, IRS potentially reduced unnecessary burdens on state officials' time and resources in responding to duplicative requests and inquiries, retesting controls that have already been evaluated, or reporting similar findings multiple times throughout a state.
|
| Social Security Administration |
Priority Rec.
The Commissioner of SSA should, in collaboration with OMB, solicit input from CMS, FBI, IRS, and state agency stakeholders on revisions to its security policy to ensure that cybersecurity requirements for state agencies are consistent with other federal agencies and NIST guidance to the greatest extent possible and document the SSA's rationale for maintaining any requirements variances. (Recommendation 10) |
SSA agreed with and has taken steps to implement this recommendation. As of February 2023, SSA revised its security policy to further align with security control guidance from the National Institute of Standards and Technology (NIST) and based on input from federal and state agencies. In April 2022, the agency updated SSA's Technical System Security Requirements (TSSR) to further align security controls with guidance from NIST Special Publication 800-53. As a result, SSA addressed most of the variances with other federal agencies' requirements that GAO originally identified. Subsequently, SSA has continued to discuss with officials from CMS, FBI, and state agencies inconsistent cybersecurity standards, security control selection, and control tailoring. By taking these steps, SSA potentially reduced unnecessary burdens on state officials' time and resources in responding to variances from multiple federal agencies' cybersecurity requirements.
|
| Social Security Administration | The Commissioner of SSA should fully develop policies for coordinating with state agencies on the use of prior findings from relevant cybersecurity assessments conducted by other organizations. (Recommendation 11) |
As of February 2022, SSA updated its policies for cybersecurity assessments to include use of prior findings from relevant assessments conducted by other organizations. Specifically, SSA updated its Technical System Security Requirements to include the review of third-party assessment findings as part of the assessment review process. By implementing this recommendation, SSA may potentially reduce unnecessary burdens on state officials' time and resources in responding to overlapping or duplicative requests and inquiries, reviewing controls that have already been evaluated, or reporting similar findings.
|
| Social Security Administration |
Priority Rec.
The Commissioner of SSA should revise its assessment policies to maximize coordination with other federal agencies to the greatest extent practicable. (Recommendation 12) |
SSA agreed with and has taken steps to implement this recommendation. As of February 2023, SSA revised its assessment policy and related procedures to improve coordination with other federal agencies. In April 2022, SSA updated its Technical System Security Requirements (TSSR) to note that SSA would leverage assessment results produced by an independent third-party, including CMS, FBI, and IRS. To do so, SSA requires that the third-party assessments utilize the same scope, depth, breadth of an SSA assessment. By taking these steps, SSA may reduce unnecessary burdens on state officials' time and resources in responding to duplicative requests and inquiries, retesting controls that have already been evaluated, or reporting similar findings.
|
