Spectrum IT Modernization: NTIA Should Fully Incorporate Cybersecurity and Interoperability Practices
Fast Facts
The National Telecommunications and Information Administration is responsible for managing federal use of the radio-frequency spectrum. The radio-frequency spectrum is a scarce resource used to support commercial and government activities such as wireless internet and air traffic control.
NTIA is working to modernize its spectrum management IT systems but hasn't fully followed leading practices for doing so. For example, it hasn't completed an organization-wide risk assessment. This, and other practices, would enable NTIA to identify, track, mitigate, and reduce cybersecurity risks and more.
Our recommendations address these and other issues.

Highlights
What GAO Found
The National Telecommunications and Information Administration (NTIA) is responsible for managing federal use of radio frequency spectrum. It is now more than three years into a planned modernization of its spectrum IT systems. In December 2024, NTIA awarded two contracts totaling $110 million to support the modernization. The first task order planned under these contracts is expected to include a program roadmap and schedule. Accordingly, NTIA will continue to rely on existing legacy IT systems for the near future.
In planning the modernization, NTIA implemented many leading cybersecurity practices but partially implemented or did not address other such practices. For example, it took steps to categorize and manage risks to its legacy spectrum IT systems. In addition, NTIA has defined key requirements for its cloud service provider. However, it has not fully developed a risk management strategy and has not completed an organization-wide risk assessment. Further, while it has developed system security plans that address most required elements (see fig.), these plans were not always current. Also, in its cloud access management policies, NTIA did not fully define user privilege levels for its systems. Fully implementing leading practices can enable NTIA to identify, track, mitigate, and reduce cybersecurity risks during the remainder of its modernization effort.
Assessment of NTIA Spectrum IT System Security Plan Elements
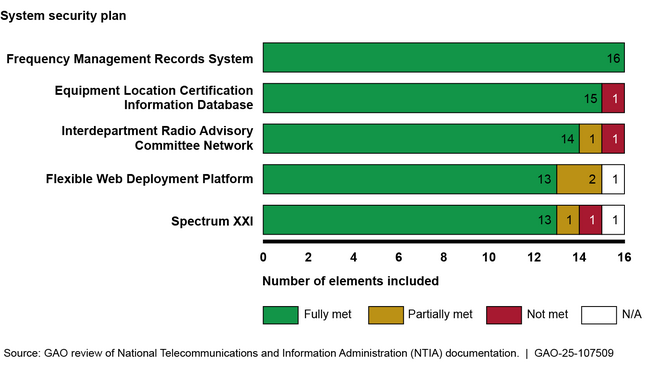
Regarding interoperability planning, NTIA met most interagency collaboration and data standards leading practices. In planning its modernization, NTIA incorporated all of GAO's eight leading practices for collaboration with its partner agencies, such as defining common outcomes and including relevant partner agency participants. NTIA also fully implemented three of five leading practices for data governance. For example, its ongoing replacement of its data standard, an important step in its modernization effort, involved stakeholders in key decisions. However, it has not developed a data governance plan that details how conflicts resulting from use of the new standard will be resolved and defines roles and responsibilities for the remaining implementation and maintenance of the standard. Until NTIA completes such a plan, NTIA and its partners may face issues in exchanging and processing spectrum IT data.
Why GAO Did This Study
Use of the radio frequency spectrum is vital to a wide variety of commercial and government activities. NTIA currently manages federal spectrum by relying on IT systems that are out of date and present usability challenges. In 2021, Congress required NTIA to create a plan for modernizing its spectrum IT systems.
As part of the same legislation, Congress required GAO to biennially review NTIA's efforts to modernize its spectrum IT systems. This review examines the extent to which NTIA's plans to modernize its spectrum IT infrastructure incorporated leading practices for (1) cybersecurity and (2) interoperability.
To do so, GAO compared NTIA modernization planning against selected practices for risk management, systems security, and cloud security. GAO compared NTIA information on interagency collaboration and data standard development against leading practices identified in prior GAO work to evaluate support for organizational interoperability. GAO also interviewed relevant NTIA officials.
Recommendations
GAO is making five recommendations to NTIA to implement leading practices on completing an organization-wide risk assessment, developing a risk strategy, maintaining current system security plans, defining cloud access management procedures, and developing a data governance plan. NTIA concurred with the recommendations and stated it will develop an action plan to implement them.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| National Telecommunications and Information Administration |
Priority Rec.
The NTIA Administrator should direct the IT Division in the Office of Policy Coordination and Management to work with the Office of Spectrum Management to develop an organizational risk management strategy that includes a determination of organizational risk tolerance, acceptable risk assessment methodologies, and details on strategies for responding to risks (such as risk acceptance, mitigation, or avoidance). (Recommendation 1) |
NTIA agreed with this recommendation and stated in May 2025 that it will prepare a formal action plan to address it.
|
| National Telecommunications and Information Administration |
Priority Rec.
The NTIA Administrator should direct the IT Division in the Office of Policy Coordination and Management to work with the Office of Spectrum Management to develop an organizational risk assessment that leverages aggregated information from system-level risk assessment results and risk considerations relevant at the organization level. (Recommendation 2) |
NTIA agreed with this recommendation and stated in May 2025 that it will prepare a formal action plan to address it.
|
| National Telecommunications and Information Administration | The NTIA Administrator should direct the IT Division in the Office of Policy Coordination and Management to work with the Department of Commerce and the NTIA Office of Spectrum Management to ensure and document that system security plans for NTIA's spectrum IT systems are reviewed, at a minimum, annually, and include logs detailing the date of review and resulting changes. (Recommendation 3) |
NTIA agreed with this recommendation and stated in May 2025 that it will prepare a formal action plan to address it.
|
| National Telecommunications and Information Administration |
Priority Rec.
The NTIA Administrator should direct the IT Division in the Office of Policy Coordination and Management to work with the Office of Spectrum Management to fully document identity, credential, and access management procedures for its cloud systems, including identification of authorized users and their roles, and associated access privileges, for each of its spectrum IT legacy systems. (Recommendation 4) |
NTIA agreed with this recommendation and stated in May 2025 that it will prepare a formal action plan to address it.
|
| National Telecommunications and Information Administration |
Priority Rec.
The NTIA Administrator should direct the IT Division in the Office of Policy Coordination and Management to work with the Office of Spectrum Management to specify a time frame for developing a data governance plan that resolves conflicts related to the application of NTIA's new data standard and defines roles and responsibilities for making decisions regarding the standard. (Recommendation 5) |
NTIA agreed with this recommendation and stated in May 2025 that it will prepare a formal action plan to address it.
|
