Defined Contribution Plans: Federal Guidance Could Help Mitigate Cybersecurity Risks in 401(k) and Other Retirement Plans
Fast Facts
In 2018, about 106 million people participated in employer-sponsored defined contribution retirement plans, such as 401(k) plans. Assets in these plans were worth about $6.3 trillion.
A host of plan administrators share the personal information used to administer these plans via the internet, which can lead to significant cybersecurity risks. In some cases, there is no federal guidance about how to mitigate these risks.
The Department of Labor hasn't clarified whether plan administrators are responsible for mitigating cybersecurity risks and hasn’t set minimum expectations for protecting personal information. We recommended that the DOL do so.

Highlights
What GAO Found
In their role administering private sector employer-sponsored defined contribution (DC) retirement plans, such as 401(k) plans, plan sponsors and their service providers—record keepers, third party administrators, custodians, and payroll providers—share a variety of personally identifiable information (PII) and plan asset data among them to assist with carrying out their respective functions (see figure). The PII exchanged for DC plans typically include participant name, Social Security number, date of birth, address, username/password; plan asset data typically includes numbers for both retirement and bank accounts. The sharing and storing of this information can lead to significant cybersecurity risks for plan sponsors and their service providers, as well as plan participants.
Data Sharing Among Plan Sponsors and Service Providers in Defined Contribution Plans
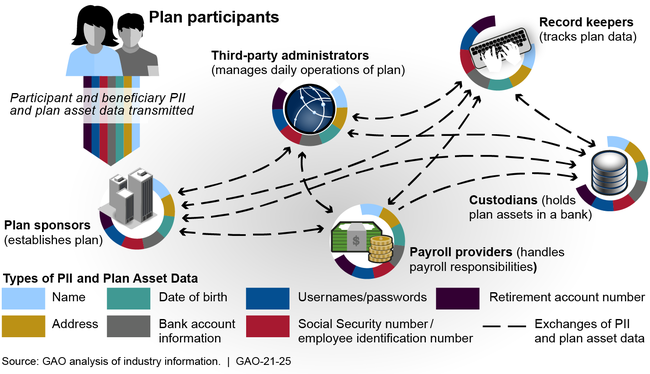
Federal requirements and industry guidance exist that could mitigate cybersecurity risks in DC plans, such as requirements that pertain to entities that directly engage in financial activities involving DC plans. However, not all entities involved in DC plans are considered to have such direct engagement, and other cybersecurity mitigation guidance is voluntary. Federal law nevertheless requires plan fiduciaries to act prudently when administering plans. However, the Department of Labor (DOL) has not clarified fiduciary responsibility for mitigating cybersecurity risks, even though 21 of 22 stakeholders GAO interviewed expressed the view that cybersecurity is a fiduciary duty. Further, DOL has not established minimum expectations for protecting PII and plan assets. DOL officials told GAO that the agency intends to issue guidance addressing cybersecurity-related issues, but they were unsure when it would be issued. Until DOL clarifies responsibilities for fiduciaries and provides minimum cybersecurity expectations, participants' data and assets will remain at risk.
Why GAO Did This Study
Cyber attacks against information systems (IT) are perpetuated by individuals or groups with malicious intentions, from stealing identities to appropriating money from accounts. DC plans, which allow individuals to accumulate tax-advantaged retirement savings, increasingly rely on the internet and IT systems for their administration. Accordingly, the need to secure these systems has become paramount. Ineffective data security controls can result in significant risks to plan data and assets. In 2018, DC plans enrolled 106 million participants and held nearly $6.3 trillion in assets, according to DOL.
This report examines (1) the data that sponsors and providers exchange during the administration of DC plans and their associated cybersecurity risks, and (2) efforts to assist sponsors and providers to mitigate cybersecurity risks during the administration of DC plans. GAO interviewed key entities involved with DC plans, such as sponsors and record keepers, DOL officials and industry stakeholders; and reviewed relevant federal laws, regulations, and guidance.
Recommendations
GAO is making two recommendations to DOL to formally state whether it is a fiduciary's responsibility to mitigate cybersecurity risks in DC plans and to establish minimum expectations for addressing cybersecurity risks in DC plans. DOL agreed with GAO's second recommendation but did not state whether it agreed or disagreed with the first one. GAO believes both recommendations are warranted.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status |
|---|---|---|
| Department of Labor | The Secretary of Labor should formally state whether cybersecurity for private sector employer-sponsored defined contribution retirement plans is a plan fiduciary responsibility under ERISA. (Recommendation 1) |
DOL neither agreed nor disagreed with this recommendation. The agency noted that plan fiduciaries must act prudently and solely in the interest of plan participants and beneficiaries, and that these duties require plan fiduciaries to take appropriate precautions to mitigate risks of malfeasance to their plans, whether cyber or otherwise. DOL also cited existing regulations on electronic records and electronic disclosures that include provisions to ensure systems are safe and personal information is protected. In April 2021, DOL issued new guidance for plan sponsors, plan fiduciaries, record keepers and plan participants on best practices for maintaining cybersecurity, including tips on how to protect the retirement benefits of America's workers. DOL issued three forms of cybersecurity guidance: 1) Tips for Hiring a Service Provider; 2) Cybersecurity Program Best Practices; and 3) Online Security Tips. Within Cybersecurity Program Best Practices, DOL states that "responsible plan fiduciaries have an obligation to ensure proper mitigation of cybersecurity risks," and "the Employee Benefits Security Administration has prepared the following best practices for use by recordkeepers and other service providers responsible for plan-related IT systems and data, and for plan fiduciaries making prudent decisions on the service providers they should hire." DOL has implemented this recommendation with these actions, which serve as a statement describing the responsibility of plan fiduciaries under ERISA to include mitigating cybersecurity risk in retirement plans.
|
| Department of Labor | The Secretary of Labor should develop and issue guidance that identifies minimum expectations for mitigating cybersecurity risks that outline the specific requirements that should be taken by all entities involved in administering private sector employer-sponsored defined contribution retirement plans. (Recommendation 2) |
DOL agreed that increasing awareness of fiduciaries' duties under ERISA with respect to cybersecurity would be helpful. In April 2021, DOL issued new guidance for plan sponsors, plan fiduciaries, record keepers and plan participants on best practices for maintaining cybersecurity, including tips on how to protect the retirement benefits of America's workers. DOL issued three forms of cybersecurity guidance: 1) Tips for Hiring a Service Provider; 2) Cybersecurity Program Best Practices; and 3) Online Security Tips. Within Cybersecurity Program Best Practices, DOL states that plans' service providers should: have a formal, well documented cybersecurity program; conduct prudent annual risk assessments; have reliable annual third party audit of security controls; have strong access control procedures; conduct periodic cybersecurity awareness training; encrypt sensitive data; implement strong technical controls, among other items. Within Tips For Hiring a Service Provider with Strong Cybersecurity Practices, DOL indicated that plan sponsors should use service providers that follow strong cybersecurity practices; the guidance provides information on how plan administrators are to evaluate providers' cybersecurity posture. In 2023, DOL officials reported that they have implemented an initiative auditing the cybersecurity hygiene and procedures of all defined contribution plans and their service providers under investigation. DOL noted that it concentrates its limited resources on investigations of retirement and health plans and service providers involved in cybersecurity breaches that lead to loss of plan assets, Personally Identifiable Information (PII), and Protected Health Information (PHI). In 2024, DOL officials updated information on its cybersecurity audit initiative. DOL noted that in these audits, it investigates the cybersecurity framework of the plans, plan sponsors and/or service providers, reviewing independent third-party audits and assessments obtained by the plans and service providers. DOL indicated that that the two frameworks they see regularly are from the National Institute of Standards and Technology (NIST) and HIPAA HITECH. As part of its audits, DOL reviews plans and service providers in accordance with the standards they adopted and look at independent third-party audits and assessments to identify whether the plan is following its documented framework. DOL also looks to these reports for any risks and vulnerabilities that have been identified to determine whether the plans or service providers have addressed these concerns. DOL officials noted that implementing all the steps outlined in the agency's "Cybersecurity Program Best Practices" would be strong evidence of a prudent process at the plan or service provider. DOL officials noted that if a plan administrator did not implement one of the steps in the Best Practices, they should demonstrate to DOL why the step was not applicable to their circumstances. The actions DOL has taken as of November 2024 partially address the recommendation. To fully implement it, DOL should take steps to define a minimum set of expectations for mitigating cybersecurity risks in plans and specific actions plan administrators and fiduciaries would be responsible for implementing to protect their systems and data. For example, DOL could adopt existing cybersecurity standards, such as the NIST framework, other frameworks outlined in the 2016 ERISA Advisory Council Report, or the standards used to safeguard data and personal identifiable information (PII) in the financial sector. Without doing so, DOL cannot ensure that participants' and beneficiaries' data or benefits are going to be protected. In August 2025, the agency reported that new political leadership at EBSA is considering how to address this recommendation.
|
