Cloud Security: Selected Agencies Need to Fully Implement Key Practices
Fast Facts
Cloud services—on-demand access to shared resources such as networks, servers, and data storage—can help federal agencies deliver better IT services for less money. But without effective security measures, these services can make agencies vulnerable to risks such as cyberattacks.
We looked at how four agencies implemented key cloud security practices—like having a plan to respond to incidents. While the agencies implemented some of the security practices, none of them fully implemented all of the practices for their systems.
We made 35 recommendations to the agencies to fully implement key cloud security practices.

Highlights
What GAO Found
The four selected agencies—the Departments of Agriculture, Homeland Security (DHS), Labor, and the Treasury—varied in their efforts to implement the six key cloud security practices that GAO evaluated. Specifically, three agencies fully implemented three practices for most or all of their selected systems, while another agency fully implemented four practices for most or all of its systems. However, the agencies partially implemented or did not implement the other practices for the remaining systems (see figure).
Agencies' Implementation of the Key Cloud Security Practices for Each of the Selected Systems
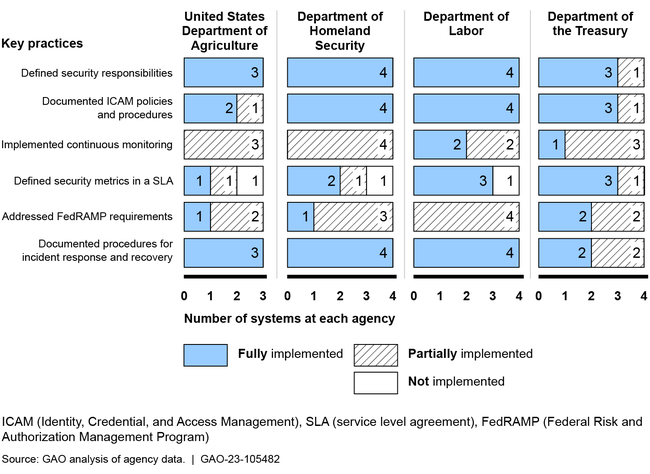
For example, the agencies partially implemented the practice regarding continuous monitoring for some or all of the systems. Although the agencies developed a plan for continuous monitoring, they did not always implement their plans. In addition, agencies partially implemented or did not implement the practice regarding service level agreements for some of the systems. Specifically, agencies' service level agreements did not consistently define performance metrics, including how they would be measured, and the enforcement mechanisms.
Agency officials cited several reasons for their varied implementation of the key practices, including acknowledging that they had not documented their efforts to address the requirements. Until these agencies fully implement the cloud security key practices identified in federal policies and guidance, the confidentiality, integrity, and availability of agency information contained in these cloud systems is at increased risk.
Why GAO Did This Study
Cloud computing provides agencies with potential opportunities to obtain IT services more efficiently; however, if not effectively implemented, it also poses cybersecurity risks. To facilitate the adoption and use of cloud services, the Office of Management and Budget and other federal agencies have issued policies and guidance on key practices that agencies are to implement to ensure the security of agency systems that leverage cloud services (i.e., cloud systems).
This report evaluates the extent to which selected agencies have effectively implemented key cloud security practices. To do so, GAO selected 15 cloud systems across four agencies (Agriculture, DHS, Labor, and Treasury), representing a broad range of services. GAO selected these agencies based on several factors, including the number of reported IT investments leveraging cloud computing. GAO compared relevant agency documentation against six key practices identified in federal policies and guidance. GAO rated each agency as having fully, partially, or not implemented each practice for the selected systems.
Recommendations
GAO is making 35 recommendations to four agencies to fully implement key cloud security practices. DHS concurred with the recommendations. Agriculture, Labor, and Treasury neither agreed nor disagreed with the recommendations. DHS, Labor, and Treasury described actions taken or planned to address the recommendations.
Recommendations for Executive Action
| Agency Affected | Recommendation | Status Sort descending |
|---|---|---|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency fully documents its procedures for responding to and recovering from security and privacy incidents for its SaaS system 1. (Recommendation 34) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Labor | The Secretary of Labor should ensure that the agency provides authorization letters to the FedRAMP PMO upon issuance of the authorization. (Recommendation 24) |
Open
In September 2023, the agency stated that it had provided authorization letters to the Federal Risk and Authorization Management Program (FedRAMP) program management office (PMO). However, as of February 2024, the agency has not provided evidence showing that it had provided authorization letters to the FedRAMP PMO upon issuance of the authorization. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency fully implements continuous monitoring for its selected SaaS system 1, to include reviewing the continuous monitoring deliverables from the CSP and committing to a time frame to review audit logs. (Recommendation 3) |
Open
In September 2023, Agriculture stated that they plan to review continuous monitoring reports from the cloud service provider (CSP) on a monthly basis. In addition, the officials stated that they plan to document their review using a continuous monitoring checklist. In January 2024, officials stated that the CSP's continuous monitoring deliverables at the departmental level. However, as of February 2024, we have not received documentation demonstrating that these reviews are performed. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency fully documents its procedures for responding to and recovering from security and privacy incidents for its SaaS system 2. (Recommendation 35) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements the FedRAMP requirements for its selected PaaS system, to include issuing an authorization for the cloud service. (Recommendation 14) |
Open
The agency stated that through its responsibilities and activities on the Federal Risk and Authorization Management Program's (FedRAMP) Joint Authorization Board, it ensures the cloud service provider meets all of the program's requirements. According to DHS officials, components that leverage a cloud service provider (CSP) with an authorization issued by the board are required to perform a risk assessment and issue an agency authorization. However, as of February 2024, we have not received evidence that the agency had issued an authorization for the CSP used as part of its selected PaaS system. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency fully implements continuous monitoring for its selected SaaS system 2, to include reviewing the continuous monitoring deliverables from the CSP. (Recommendation 4) |
Open
In September 2023, Agriculture stated that they plan to review continuous monitoring reports from the cloud service provider (CSP) on a monthly basis. In addition, the officials stated that they plan to document their review using a continuous monitoring checklist. In January 2024, officials stated that the CSP's continuous monitoring deliverables at the departmental level. However, as of February 2024, we have not received documentation demonstrating that these reviews are performed. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements the FedRAMP requirements for its selected SaaS system 2, to include issuing an authorization for the cloud service. (Recommendation 15) |
Open
The agency stated that through its responsibilities and activities on the Federal Risk and Authorization Management Program's Joint Authorization Board, the agency ensures the cloud service provider (CSP) meets all of the program's requirements. According to DHS officials, components that leverage a CSP with an authorization issued by the board are required to perform a risk assessment and issue an agency authorization. However, as of February 2024, we have not received evidence that the agency had issued an authorization for the cloud service used as part of its selected SaaS system 2. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should commit to a date for completing efforts to define the delineation of security responsibilities between the agency and the CSP for its selected SaaS system 2. (Recommendation 26) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency's contracts with CSPs include requirements for the service providers to comply with security authorization FedRAMP requirements. (Recommendation 16) |
Open
Agency officials stated that they are updating their contract language to include additional details and clarifying requirements specifying compliance with the Federal Risk and Authorization Management Program's authorization requirements. The agency officials estimated that they would complete these efforts in fiscal year 2024. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency commits to a time frame for when it plans to require the use of multifactor authentication for its selected SaaS system 1, and implements the plan. (Recommendation 27) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency fully implements continuous monitoring for its selected PaaS system, to include implementing its plans for continuous monitoring of the security controls that are the agency's responsibility and reviewing the continuous monitoring deliverables from the CSP. (Recommendation 28) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency's contracts with CSPs include requirements for the service providers to comply with FedRAMP security authorization requirements. (Recommendation 7) |
Open
In September 2023, Agriculture officials stated that they planned to coordinate with the agency's Office of Contracting and Procurement to ensure that contracts with cloud service providers (CSP) include requirements for them to comply with the Federal Risk and Authorization Management Program (FedRAMP) security authorization requirements. In February 2024, USDA officials stated that the agency had updated its contracts with CSPs. The agency provided documentation, including its contracting desk book and the agency's cloud strategy. However, our review of these documents found that they did not include policies to ensure that the agency's contracts with CSPs include requirements for the service providers to comply with FedRAMP security authorization requirements. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency fully implements continuous monitoring for its selected SaaS system 2, to include implementing its plans for continuous monitoring of the security controls that are the agency's responsibility and documenting the use of vulnerability management procedures and tools to monitor the agency's cloud infrastructure. (Recommendation 29) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements continuous monitoring for its selected SaaS system 2, to include implementing its plans for continuous monitoring of the security controls that are the agency's responsibility. (Recommendation 8) |
Open
In May 2023, the agency provided evidence demonstrating that it had accepted the system as part of its ongoing authorization program. According to the agency, to remain in the program, the agency is required to perform continuous monitoring of the security controls. However, as of February 2024, we have not received evidence demonstrating that the agency had monitored the security controls that are the agency's responsibility. We will follow-up with the agency to obtain supporting evidence.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency fully implements continuous monitoring for its selected SaaS system 1, to include reviewing the continuous monitoring deliverables from the CSP. (Recommendation 30) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements continuous monitoring for its selected IaaS system, to include performing a regular review of the continuous monitoring deliverables from the CSP. (Recommendation 9) |
Open
The agency stated that through its role on the Federal Risk and Authorization Management Program's Joint Authorization Board, it has performed a regular review of the continuous monitoring deliverables from the cloud service provider. In September 2023, the agency stated that the components and programs leveraging the service provider are responsible for reviewing the board's continuous monitoring reports. However, as of February 2024 we have not received evidence demonstrating that the officials responsible for the selected IaaS system had reviewed these reports. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency's service level agreements with CSPs define the enforcement mechanisms. (Recommendation 31) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements continuous monitoring for its selected PaaS system, to include implementing its process to review the continuous monitoring deliverables from the CSP. (Recommendation 10) |
Open
The agency stated that through its role on the Federal Risk and Authorization Management Program's Joint Authorization Board, it has performed a regular review of the continuous monitoring deliverables from the cloud service provider. In September 2023, the agency stated that the components and programs leveraging the service provider are responsible for reviewing the board's continuous monitoring reports. However, as of February 2024 we have not received evidence demonstrating that the officials responsible for the selected PaaS system had reviewed these reports. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Labor | The Secretary of Labor should ensure that the agency fully implements the FedRAMP requirements, to include issuing an authorization for the cloud service for its selected PaaS system. (Recommendation 21) |
Open
In September 2023, the agency stated that it has issued an authorization for the cloud service for its selected PaaS system. The agency provided its authorization for the agency's system; however, it did not clearly identify the authorization for the associated cloud service provider. We plan to follow-up with the agency to obtain the relevant documentation, and we will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency fully implements the FedRAMP requirements, to include performing a review and risk analysis of the CSPs' FedRAMP security packages for its selected SaaS system 1. (Recommendation 32) |
Open
In January 2024, we requested an update from the agency on its efforts to address our recommendation. However, as of February 2024, the agency has not provided an update. When we confirm what actions the agency has taken in response to this recommendation, we will provide updated information.
|
| Department of Labor | The Secretary of Labor should ensure that the agency fully implements the FedRAMP requirements, to include issuing an authorization for the cloud service for its selected SaaS system 1. (Recommendation 22) |
Open
In September 2023, the agency stated that it has issued an authorization for the cloud service for its selected SaaS system 1. The agency provided its authorization for the agency's system; however, it did not clearly identify the authorization for the associated cloud service provider. We plan to follow-up with the agency to obtain the relevant documentation, and we will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Labor | The Secretary of Labor should ensure that the agency fully implements the FedRAMP requirements, to include issuing an authorization for each of the cloud services and performing a review and risk analysis of the CSPs' FedRAMP security packages for its selected SaaS system 2. (Recommendation 23) |
Closed – Implemented
In September 2023, the agency stated that according to the agency's policy, an annual review of assessments performed by third party assessment organizations (3PAO) is sufficient to document review of the cloud service providers (CSP) for its selected SaaS system 2. In February 2024, the agency provided documentation of the policy. Further, the agency provided evidence demonstrating that that the agency had completed a review and risk assessment of the cloud service, and that the agency had accepted the Federal Risk and Authorization Management Program authorization for the CSPs. As a result of these efforts, the agency has improved its ability to fully identify the security risk of the system.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements the FedRAMP requirements for its selected IaaS system, to include issuing an authorization for the CSP and providing an authorization letter to the FedRAMP PMO. (Recommendation 13) |
Closed – Implemented
In September 2023, the Department of Homeland Security provided evidence that it had issued an authorization for the cloud service provider (CSP) used as part of its selected IaaS system. In addition, the agency submitted evidence that it had provided an authorization letter to the Federal Risk and Authorization Management Program (FedRAMP) program management office (PMO). As a result, the agency has improved their ability to monitor the security risks of the system, including to be notified by FedRAMP of any changes to the authorization of the CSP.
|
| Department of Labor | The Secretary of Labor should ensure that the agency's contracts with CSPs include requirements for the service providers to comply with FedRAMP security authorization requirements. (Recommendation 25) |
Closed – Implemented
In February 2024, the agency provided its June 2023 policy on cybersecurity and privacy language for IT procurements. The policy provided language that the agency is to include in its contracts. In particular, the policy provided contract language that specifies that cloud service providers (CSPs) used by contractors must be authorized through the Federal Risk and Authorization Management Program (FedRAMP). In addition, the policy states that CSPs' FedRAMP authorization packages must be reviewed and approved by the agency prior to use. As a result of these efforts, the agency has reduced the risk that the CSPs used by the agency will not fully implement FedRAMP requirements.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency's service level agreements with CSPs define performance metrics, including how they are measured and the enforcement mechanisms. (Recommendation 5) |
Closed – Implemented
In September 2023, Agriculture officials stated that they planned to coordinate with the agency's Office of Contracting and Procurement to incorporate service level agreement in the agency's future contracts for cloud services. In February 2024, USDA officials stated that the agency had incorporated the requirements into its contractual process. The agency provided supporting documentation including a departmental regulation on cloud computing. The regulation requires that the agency's cloud computing service acquisition vehicles include service level agreements (SLA). According to the regulation, these SLAs are to include, among other things, security monitoring, performance measurements, and remediation for noncompliance. As a result of these efforts, the agency has increased its ability to mitigate risk and to ensure that its cloud services perform as intended.
|
| Department of Labor | The Secretary of Labor should ensure that the agency fully implements continuous monitoring for its selected IaaS system, to include implementing its plans for continuous monitoring of the security controls that are the agency's responsibility. (Recommendation 17) |
Closed – Implemented
In September 2023, the agency stated that it has verified that annual assessments of cloud service providers are formally documented, reviewed, and signed by appropriate levels of management. In February 2024, the agency provided a security assessment report for its selected IaaS system. The report provided evidence that the agency had fully implemented continuous monitoring for its selected IaaS system, including the monitoring of the security controls that are the agency's responsibility. As a result of these efforts, the agency has improved its ability to have ongoing awareness of any changes to the security and privacy posture of the system.
|
| Department of Labor | The Secretary of Labor should ensure that the agency fully implements continuous monitoring for its selected PaaS system, to include reviewing the continuous monitoring deliverables from the CSP. (Recommendation 18) |
Closed – Implemented
In September 2023, the agency stated that it documented its reviews of cloud service providers (CSP) through its cybersecurity policy portfolio and that the agency performs monthly information security continuous monitoring activities to validate that requirements are met. In February 2024, the agency provided documentation demonstrating that it had reviewed the continuous monitoring deliverables from the CSP for its selected PaaS system. As a result of these efforts, the agency has improved its ability to have ongoing awareness of any changes to the security and privacy posture of the system.
|
| Department of Labor | The Secretary of Labor should ensure that the agency fully implements the FedRAMP requirements, to include performing a review and risk analysis of the CSPs' FedRAMP security packages for its selected IaaS system. (Recommendation 20) |
Closed – Implemented
In September 2023, the agency stated that according to the agency's policy, an annual review of assessments performed by third party assessment organizations is sufficient to document review of cloud service providers (CSP). In February 2024, the agency provided documentation of the policy. In addition, the agency provided documentation demonstrating that it had reviewed the CSP's authorization package. As a result of these efforts, the agency has improved its ability to fully identify the security risk of the system.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency fully implements continuous monitoring for its selected SaaS system 1, to include implementing its process to review the continuous monitoring deliverables from the CSP. (Recommendation 11) |
Closed – Implemented
In October 2023, the agency provided evidence that it had reviewed the continuous monitoring deliverables from the cloud service provider (CSP) for its selected SaaS system 1. As a result, the agency has improved its ability to have ongoing awareness of any changes to the security and privacy posture of the system.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency fully documents the access authorizations for its selected PaaS system. (Recommendation 1) |
Open – Partially Addressed
In September 2023, Agriculture officials described their plans for addressing our recommendation. Specifically, the officials stated that they will review their existing identity, credential and access management procedures, and will document the access authorizations for the selected system. In January 2024, the agency provided documentation of its procedures for the system's authorization process. However, the procedures did not document the access authorizations for the system. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of the Treasury | The Secretary of the Treasury should ensure that the agency's contracts with CSPs include requirements for the service providers to comply with FedRAMP security authorization requirements. (Recommendation 33) |
Open – Partially Addressed
We reported that the agency had not required CSPs to comply with FedRAMP requirements for its SaaS system 1, and SaaS system 2. In January 2024, the agency provided evidence that it had updated the contract for its SaaS system 2, to include the requirements. However, the agency did not provide evidence that it had updated its contract for SaaS system 1, or that it had ensured that the agency's contracts with CSPs include the requirements. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Homeland Security | The Secretary of Homeland Security should ensure that the agency's service level agreements with CSPs define performance metrics, including how they are measured and the enforcement mechanisms. (Recommendation 12) |
Open – Partially Addressed
The agency stated that it ensures that agency service level agreements (that define performance metrics) are in place whenever possible, including how they are measured and enforced. In September 2023, the agency provided documentation of policies and guidance it uses for acquiring cloud services. For example, the agency provided a policy that includes the minimum requirements that are to be included in contract language. However, the policies and guidance did not address how the agency ensures that service level agreements with cloud service providers define performance metrics, including how they are measured and the enforcement mechanisms. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency fully implements continuous monitoring for its selected PaaS system, to include reviewing the continuous monitoring deliverables from the CSP and committing to a time frame to review audit logs. (Recommendation 2) |
Open – Partially Addressed
In September 2023, Agriculture officials described their plans for addressing our recommendation. Specifically, the officials stated that they plan to develop and adopt procedures that detail the process for implementing and documenting continuous monitoring for its selected system. According to the officials, the procedures would include the review of continuous monitoring deliverables from the cloud service provider, and the frequency for review of audit logs. In January 2024, the agency provided documentation of its continuous monitoring procedures. The procedures including, among other things, steps for reviewing the continuous monitoring deliverables from the CSP. However, the agency did not provide documentation showing that these efforts were implemented. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Agriculture | The Secretary of Agriculture should ensure that the agency provides the authorization letter to the FedRAMP PMO for its selected SaaS system 2. (Recommendation 6) |
Open – Partially Addressed
In September 2023, Agriculture officials described their plans for addressing our recommendation. Specifically, the officials stated that they plan to develop procedures, including guidance, for addressing the Federal Risk and Authorization Management Program (FedRAMP) requirements. In February 2024, the agency provided its FedRAMP Standard Operating Procedures. The procedures include requirements for providing authorization letters to the FedRAMP program management office (PMO). However, the agency did not provide evidence that it had provided the letter to FedRAMP PMO for its selected SaaS system 2. We will continue to monitor the agency's efforts to address our recommendation.
|
| Department of Labor | The Secretary of Labor should ensure that the agency's service level agreements with CSPs define performance metrics, including how they are measured and the enforcement mechanisms. (Recommendation 19) |
Open – Partially Addressed
In September 2023, the agency stated that it reviews the service level agreements (SLA) defined by the cloud service provider (CSP). In February 2024, agency officials provided the agency's policy for system and services acquisition. According to the policy, the agency is to require that providers of external system services, which includes cloud services, comply with organizational security and privacy requirements, such as through the use of service level agreements. However, it is not clear how the agency ensures that the service level agreements define performance metrics, including how they are measured and the enforcement mechanisms. We will continue to monitor the agency's efforts to address our recommendation.
|
